Collaboration Solutions - how to select and use them securely
Author: Jose Monteagudo, CEO, Smartrev Cybersec
Collaboration Solutions - Background
During the last few months there has been a fundamental change in the way employees interact with their companies, colleagues, and teams. The pandemic has played an important role in accelerating the ubiquitous digital transformation that started a few years ago and achieved heterogeneous levels of success across major industries.
Due to the substantial risks of covid-19, companies have in some cases voluntarily decided to send their employees home and in other cases been forced to do so subject to strict requests from the local, state, or federal administrations. This dramatic change has been implemented in a matter of days or weeks.
As an example, out of the 140 million civilian workers in the US only 7 % (or roughly 9.8 million) had access to remote working benefits in 2019. Telework is also more common in the private sector than in the local, state or federal administration, based on the analysis of the 2019 National Compensation Survey (NCS) from the federal Bureau of Labor Statistics.
In this environment, collaborative solutions that enable Remote Working, or Working From Home (WFH), have experienced an unparalleled growth.
Considering the low percentage of workers with access to remote working models before the crisis and the swift change imposed by covid-19, companies have struggled to implement the right infrastructure in a timely manner to assure a secured and productive remote working environment for their employees.
In this article, we will shed some light on two important elements:
- Criteria to consider when selecting a collaborative solution
- How to use collaboration services and solutions securely
Criteria to consider when selecting a collaborative solution
Unfortunately, it seems that covid-19 will be around for a while. Probably, as many say, the working environment will never be the same in a post-covid-19 world. As a mitigation plan for this serious issue and long-term risk, companies need to adapt their infrastructure to enable workers to work remotely or even from home in a secure way.
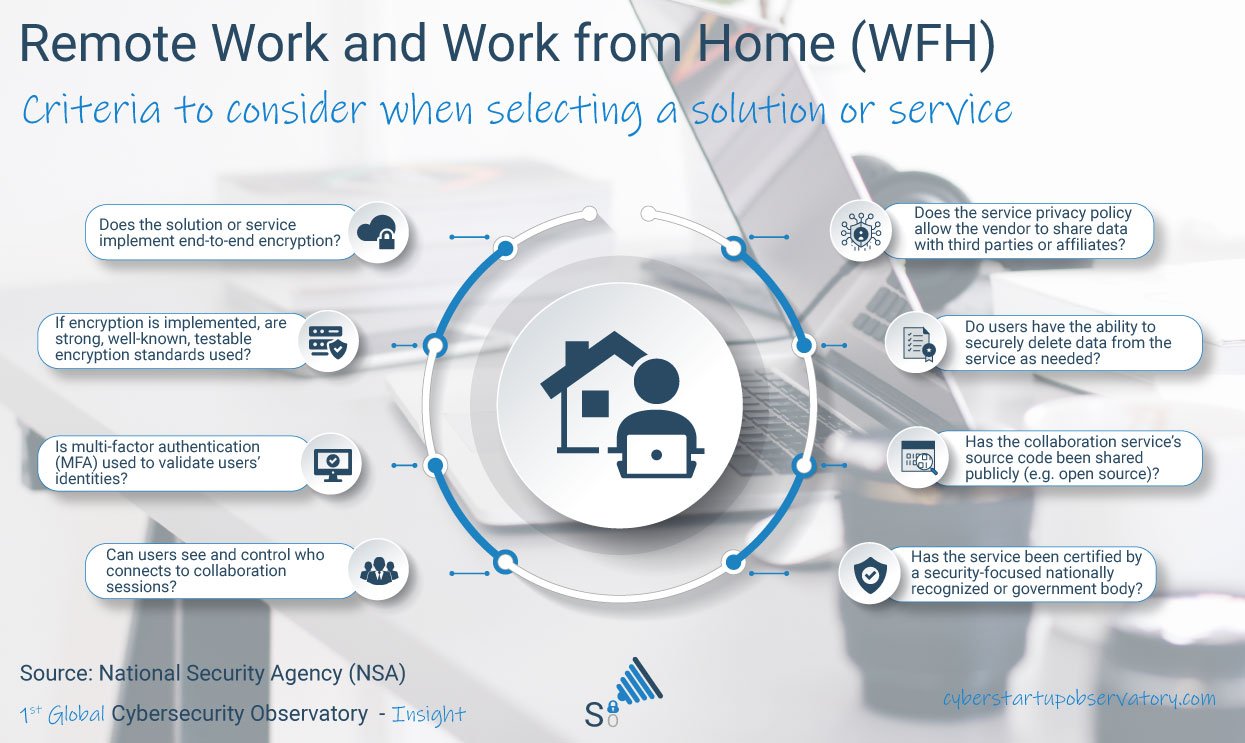
When selecting a collaborative solution, key considerations to take into account are:
- Encryption: the solution needs to implement End-to-End encryption using strong, well-known encryption standards.
- Strong Authentication: multi-factor authentication (MFA) should be used to validate user’s identities.
- Strict control of attendees: can users see and control who connects to collaboration sessions?
- Data Privacy: does the solution or service privacy policy allow the vendor to share data with third parties? And do the users have the ability to delete data securely from the service / solution and its repositories as needed?
- Trust: has the solution source’s code been shared publicly? And has it been reviewed or certified for use by a security-focused and internationally recognized body?
Going through this analysis will help organizations secure their remote workers and the company as a whole, as well as understand the risks involved in the eventual selection of a specific technology or solution provider.
How to use collaboration services and solutions securely
Once the company has decided which solution best fits into the company’s needs and risk appetite, there are a few recommendations and best practices to follow in order to create an environment as safe as possible for teleworkers.
Let’s cover the key policies to follow or implement in order to maximize privacy and security:
- Download from a safe and trustworthy website. Conduct your assessment to assure that the selected website has a good reputation and, when possible, use a download server directly from the software editor instead of using middlemen services which might include adware, spyware or other more dangerous types of malware.
- Always use encryption during your collaboration sessions.
- Use the most secure means available to send meeting invitations. Never share them publicly.
- Verify that only intended invitees are participating before beginning and throughout each session.
- Ensure that any information shared is appropriate for all the participants. Sometimes it will be needed to organize different meetings based on the level of confidentiality of the information shared. Plan taking this issue into consideration and never share information that was not approved before the meeting. Once shared you do not control it anymore.
- Ensure that the physical environment does not provide unintentional access to voice, video or data during the collaboration sessions. Remote workers should be cautious of organizing collaboration sessions at airports, restaurants, business lounges and other public places.
- Try to avoid public WIFI services. As a general rule, they are dangerous and subject to a myriad of potential attacks. Among these attacks, the most common are: snoops can infiltrate them to collect sensitive information, they are susceptible to Man-in-the-Middle Attacks, they can inject malware, or you might be even connecting to a Rogue Hotspot without even knowing it.
Collaborative Solutions - Conclusion
Covid-19 is wreaking havoc in our society and economies all around the world. The most challenging element of this crisis is the fact that we do not know how long it is going to last and the price to pay in terms of human lives lost, jobs and the amount of debt incurred by governments all around the world.
Companies need to work on a mitigation plan that addresses this uncertainty.
Technologies do exist to support social distancing and among them, collaboration solutions play a crucial role. Nevertheless, criminals leverage every single opportunity, and as a consequence, it is absolutely crucial to use these technologies responsibly. This article represents our two cents to achieve this goal.
References:
- NSA, Selecting and Safely Using Collaboration Services for Telework.
- 2019 National Compensation Survey (NCS) from the federal Bureau of Labor Statistics.
Follow Us
Collaboration Solutions: how to select and use them securely