
Cyber Forensics in The Cloud Environment
Author: David Tayouri, Cyber R&D Manager at IAI - ELTA
 The digital infrastructure landscape is evolving towards fully integrated, multifunction, cloud-delivered networking and security platforms. Today’s organizations are required to provide customers and employees with immediate, uninterrupted service regardless of where they are physically located. This transformation to digital business requires anywhere, anytime access to applications and services – many of which are located in the cloud. However, with the many advantages, this model affords come a myriad of security concerns. Enterprises seek to protect their assets from unauthorized entities while maintaining business continuity by allowing trusted devices and users to access applications hosted on-premises or in the cloud. They need to implement cloud-based security technologies in different layers to achieve this. To improve cloud security, we examine the cloud access architecture as presented in the diagram below and consider the context: who is accessing, from where, and what is the access target. For cybersecurity in general and cloud security in particular, different methods should be considered to prevent, detect, analyze, and respond to attacks. Included among them is cyber forensics.
The digital infrastructure landscape is evolving towards fully integrated, multifunction, cloud-delivered networking and security platforms. Today’s organizations are required to provide customers and employees with immediate, uninterrupted service regardless of where they are physically located. This transformation to digital business requires anywhere, anytime access to applications and services – many of which are located in the cloud. However, with the many advantages, this model affords come a myriad of security concerns. Enterprises seek to protect their assets from unauthorized entities while maintaining business continuity by allowing trusted devices and users to access applications hosted on-premises or in the cloud. They need to implement cloud-based security technologies in different layers to achieve this. To improve cloud security, we examine the cloud access architecture as presented in the diagram below and consider the context: who is accessing, from where, and what is the access target. For cybersecurity in general and cloud security in particular, different methods should be considered to prevent, detect, analyze, and respond to attacks. Included among them is cyber forensics.
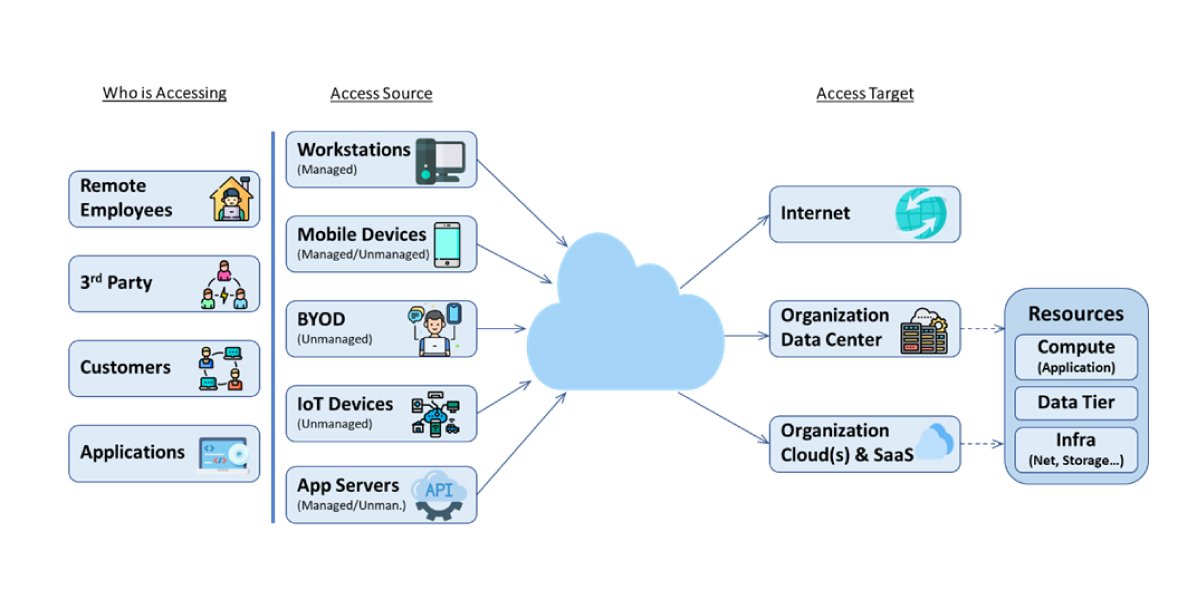
Figure 1: Cloud Access Architecture
Cyber Forensics
Digital forensics is the branch of forensics that focuses on recovering, investigating, and analyzing material found in digital devices.
Cyber forensics focuses on techniques used to track the footprints left by a cyberattack and is widely employed in incident response, malware analysis, data leak protection, and cybercrime investigations.
We refer to cloud forensics when the examined artifacts reside in the cloud.
For digital evidence to be accepted in a court of law, it must be handled in a way that prevents its tampering by cyber criminals.
The forensics process includes five phases:
- Identification – finding the evidence and noting where it is stored.
- Preservation – isolating, securing, and preserving the data, including preventing possible tampering with the evidence.
- Acquisition – retrieving the data from suspected digital assets.
- Examination – reconstructing data fragments and drawing conclusions based on the evidence found.
- Presentation – creating a record of all the data to recreate the crime scene and summarizing it for presentation in court.
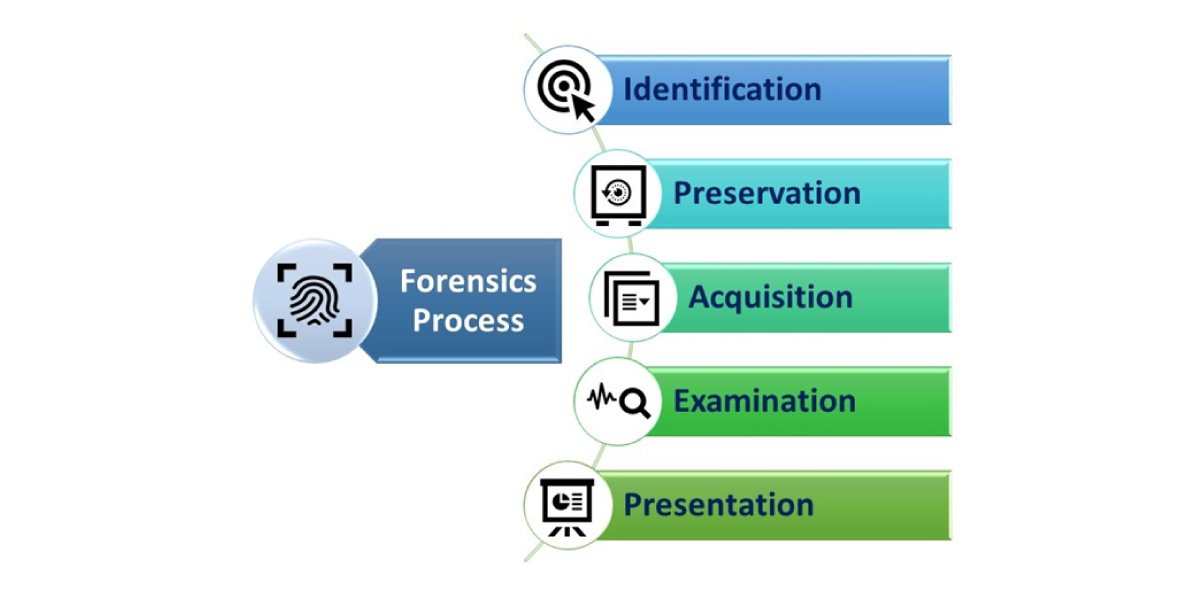
Figure 2: The Forensics Process
Cloud Forensics Challenges
Cloud forensics brings many inherent challenges in all of the above-noted phases. Following are some of the main challenges 1,2,3:
Identification
Access to the evidence in logs – in some instances, investigators do not know the data’s location due to the cloud’s distributed nature.
Volatile data – when a virtual machine (VM) is turned off or restarted, all the data is lost unless the image is stored somewhere.
Intelligence processes for real-time investigation are impossible – most providers do not reveal the specifics of their operations.
Evidence identification – in most cloud computing environments, most of the evidence is either unavailable or not generated or stored in the same way as in traditional non-cloud settings. In cloud computing, resources are usually exposed abstractly.
Application details are unavailable – private and confidential information of cloud-based software/applications used to produce records are typically inaccessible to the investigator.
Preservation
Isolating a cloud instance – in the cloud environment, it is hard to isolate the incident environment to prevent any possible evidence from tampering or alteration due to resource sharing between multiple users.
Data integrity – errors may occur in the data preservation stage in the cloud context due to multiple actors who are involved in the process.
Time synchronization – the synchronization of time can be used as a source of evidence, but the date and time stamps of the data are questionable when they are from multiple systems. Moreover, the difference in time zones between cloud servers and cloud clients can affect evidence integrity, reliability, and admissibility.
Live forensics – when evidence is collected in a cloud environment, the suspect system is still running, and data is likely changing as it is being collected. Therefore, data correctness cannot be verified.
Acquisition
Multi-tenancy – cloud service providers (CSPs) use of multiple data centers to serve multi-cloud computing customers may raise many uncertainties about customers’ data isolating and retrieving. Virtualization – extracting sound evidence from a VM is difficult due to malicious code that may circumvent VM isolation methods.
Data deletion – investigating and retrieving deleted data in a cloud computing environment is challenging because the CSPs do not use sufficiently sophisticated methods for retrieving information on deleted data. In addition, deleted data can be overwritten by another user in a shared virtual environment.
Dynamic storage – some CSPs dynamically allocate storage based on the user’s current needs. As data is deleted from the system, the storage is reallocated.
Examination
Evidence correlation – the evidence may be spread across multiple digital resources.
Crime scene reconstruction – reconstruction of the crime scene in the cloud environment to understand how illegal activities were committed may be problematic. For example, when adversaries shut down their virtual instances after committing malicious activities, reconstructing the crime scene will be impossible.
Decoupling between cloud user credentials and physical users – binding a cloud username to a physical entity to prove the physical ownership of the data attributed to the cloud username is challenging.
Cloud Forensics Guidelines
The above-mentioned challenges are emphasized due to the multi-national nature of the cloud and the lack of global standards and regulations concerning cloud forensics. Following are some guidelines that will help cope with these challenges 5,6,7:
Policy & SLA
- Have a well-documented digital forensics process. This can be part of the incident response policy and procedures, but it should cover the complete forensic investigation lifecycle.
- Predefine a set of corporate-approved forensics-enablement tools to be installed as part of any instance deployment in the cloud platform.
- Establish logging requirements for cloud platforms and set the severity level, timestamp format, and retention and rotation periods. Enable logging and auditing in the cloud environment by corporate policy.
- Define with the CSP which logs from the underlay infrastructure can be exposed during forensics examinations and how long the log retention periods are. Specify recoverability after deletion options for each type of log.
- Define data storing location(s) by agreeing with the CSP on the corporate authority to decide where all the data is stored for the deployed environment (country, state, and jurisdiction).
- Evaluate the service model supplied by the CSP being analyzed: SaaS (Software as a Service), PaaS (Platform as a Service), or IaaS (Infrastructure as a Service). The detection of an incident in a cloud environment may differ according to the model adopted for the services.
- Identify the particular data sought, relevant periods, the involved CSPs, and the utilized services.
- Interact with the CSPs’ professionals to map the incident and the extent of the damage.
- Implementing preservation techniques may require isolating cloud resources. CSPs should isolate the physical disk connected to an incident, taking into account that data from other customers sharing resources could also be copied.
- The chain of custody must start when the researcher has access to physical media. Implement contracts that allow the investigator access to the evidence, sometimes physically.
Acquisition
- Consider using the Cyber Forensic Field Triage Process Model (CFFTPM), which proposes an onsite approach for identifying, analyzing, and interpreting digital evidence in a short time frame.
- The CSP should be responsible for extracting forensics images of the physical disk or partition, or at least the virtual machine created for the client by handling the hypervisor.
- Sometimes, it may not be possible to shut down a machine to remove the disc or boot via live CD. Therefore, remote collection strategies should be established.
- Document the acquisition process, including system information, methods used, and how the data is received. This step is crucial to assure the process’ integrity.
Examination
- Consider timestamping in the collection and analysis phases.
- Regarding the logs, the experts should be familiar with the most used platforms, knowing how logs are generated so they can use a parser efficiently.
References
1 Cloud Forensics: A Review of Challenges, Solutions and Open Problems,
https://ieeexplore.ieee.org/document/7149635
2 Digital Forensic Investigation Challenges based on Cloud Computing Characteristics,
https://www.sciencepubco.com/index.php/ijet/article/view/21361
3 NIST Cloud Computing Forensic Science Challenges,
https://csrc.nist.gov/publications/detail/nistir/8006/final
4 Cybersecurity Standards for Cloud Access,
https://ieeexplore.ieee.org/document/9718230
5 Cloud Forensics - Best Practice and Challenges for Process Efficiency of Investigations and Digital Forensics,
http://icofcs.org/2013/ICoFCS-2013-003.pdf
6 IPCFA: A Methodology for Acquiring Forensically-Sound Digital Evidence in the Realm of IAAS Public Cloud Deployments,
https://scholar.dsu.edu/cgi/viewcontent.cgi?article=1367&context=theses
7 Scientific Working Group on Digital Evidence, Best Practices for Digital Evidence Acquisition from Cloud Service Providers,
https://www.swgde.org/documents/published

