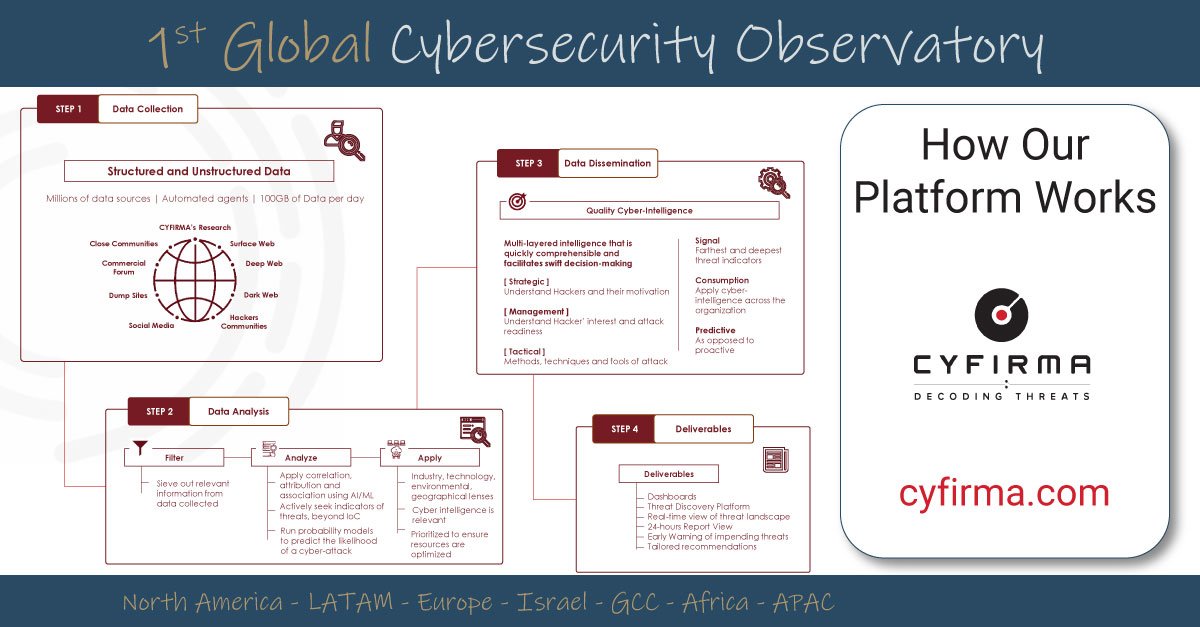
Cybersecurity Leaders - Thomas Pache
Thomas Pache is responsible for Cyber Insurance at RiskPoint. RiskPoint is a Danish Underwriting Agency offering selected risk transfer solutions with an underwriting excellence claim in Europe, focusing on Scandinavia and Germany.
Professional background and experiences
Dipl-Ing. Maschinenbau and Dipl.-Wirtschaftsing. (- 1989); Regiment Technical Officer (Captain) at the German Federal Armed Forces (-1994); Casualty/FL Underwriter with focus on technological risks at Gerling (-1998); Chief Underwriting Officer Tech (IT-Liability) at Gerling (-2004); Head of Corporate Department at Gerling Konzern Allgemeine (-2006); CMT Industry Practice Leader for Germany and Austria at Marsh (-2009); Branch Office Manager Northern and Eastern Gemany at Nassau (-2012); PI Manager Germany main focus: Tech and Cyber at AIG Insurance (-2016); Chief Underwriting Officer Tech & Cyber - Austria, Germany and Switzerland at AIG Insurance (-09/2017); Head of Cyber / Senior Underwriter at RiskPoint.
In parallel:
Author / lecturer for (DVA, MWV, MCC, BWV, Versicherungsforum, EUROFORUM, Phi, etc.); Member (Head until 10/2017) of GDV‘s cyber insurance task force; Member of GDV‘s Tech insurance project.
In the past seven years Thomas Pache has met with many Cybersecurity Leaders from different sizes of enterprises in order to understand and discuss Information Security issues and mitigation strategies of their companies to find a way to transfer remaining financial risks and make them calculable from a C-suite perspective.
Are there any common business roadblocks that prevent security practices from being implemented?
Yes, even if they are decreasing in comparison to past years, there are still quite a few roadblocks. I just want to name the two biggest ones here:
1. Considering the aspects of organization, technology, prevention and management, the C-Suite is the weakest link in the chain. The recently published management report “Cyberschutz 2019” by VdS and GDV, based on more than 5,000 cyber security self-assessments by companies, shows a positive trend-However, with 38% (100% = ideal), the management department clearly falls over the other aspects (all> 60%).
2. Despite the increasing digitization, especially of devices not connected to networks so far, the OT is often operated in a kind of parallel world and is thus beyond the control of the CISO.
How do you convey to the board the message that – with regards to cybersecurity – you can minimize the risk but you are never going to be 100 percent secure?
Since all board decisions are based on business considerations, this situation is explained most simply with two business-mathematical functions:
Examples from the past, such as Stuxnet, show that organizations can not 100% secure against state-motivated, targeted attacks. But once the board has set a desired level of security and the actual level has been determined, this results in the investment needed to achieve the goal, which can hardly be achieved economically by technology, process changes and training alone. Especially in the area of recent percentages, risk transfer solutions such as cyber insurances can also be a more economically efficient instrument for achieving goals.
Another important argument in manufacturing companies is the OT update dilemma. Here, the time required for updates counteracts the goal of an interruption-free 24/7 production.
How can security executives help C-suit better understand cybersecurity?
As stated in my previous answer, IT / cyber risks to the business should always be in business language, i.e. Key figures, to be translated. For this to be possible, a company must first identify and classify the business model-critical processes as well as their ITK dependency and vulnerability (cause-and-effect principle). Unlike with fire or currency risks, this information is usually not available for this new threat.
If this first step succeeds, all future statements of the CISO are on a solid foundation from the point of view of the management.
Ransomware and phishing are among the risks that have threatened all industries recently. From your perspective, how should companies mitigate these risks and what has worked for you?
For some time, the realization has become more and more that an absolutely reliable perimeter protection is not feasible. Therefore, the aspect of resilience and crisis response (keywords: DRP, RTO, RPO) needs to be given even more prominence. Of course, that does not mean that the perimeter protection should be neglected, but it alone is no longer enough.
Cyber risk scenarios must therefore be an integral part of each company’s contingency plans. This is especially true for the BCM. Here it would be useful - if possible - to draw up contingency plans (for example, manual control of production machines) even in the event of an ITC disruption.
Digitalization is a double-edged sword, offering benefits but also entailing serious risks. What are your thoughts on this inevitable development?
Since this development is likely to be unavoidable, as you said in your question, I believe that such risks must be systematically identified in the development of new products, business models and processes and mitigation strategies / measures must be part of the development work. Only those companies that follow this approach will be successful in the long term.
How has industry cooperation made an impact on cybersecurity?
In the context of increasing productivity, the division of labor has played a key role for many years. This started with the Kanban system from Japan, which requires in-house communication with suppliers in real time. At the present time, this is realized via digital networks, which is why both internal and cross-company networking - keyword IoT - will continue to increase. It will be important to be able to exchange data securely despite advancing technological developments and to constantly adapt the protection of communication to the changing threat.
Closing Statement
As you know, I’ve been involved with IT and cybersecurity for nearly 25 years, but I’m not a CISO or an IT expert. However, as an engineer and industrial engineer, I am very keen to improve the communication and mutual understanding between IT security experts, business economists, lawyers and insurers because I am convinced that only together can we provide a sustainable answer to these complex and rapidly changing ones. Cyber threats - keyword Dynaxity - can be found. There are currently too many wheelers claiming to have found simple solutions. Therefore, I would very much welcome an interdisciplinary exchange and discussion platform for cyber risks and their implications. So, if someone is interested in an exchange of ideas, …
Cybersecurity Leaders - Thomas Pache