5 Cyber Range solutions you should bear in mind in 2020
Author: Jose Monteagudo, CEO, Smartrev Cybersec
Cyber Range Solutions - Introduction
Over the last decade, and especially in the last three years, the threat landscape for all types of organizations, both small and medium-sized companies, has become substantially more complicated. In our mission to identify the most innovative cybersecurity solutions, the Cybersecurity Observatory has witnessed unprecedented innovative activity in this field with high-quality initiatives arising in the different innovation hubs of the world, responding to the needs of the companies to protect increasingly digital companies, as well as governments, banks and critical infrastructure. Unfortunately, we have also witnessed high rates of innovation on the other side: cyber criminals, criminal organizations, mafias and even nations have developed sophisticated tools to meet their objectives through cyber-attacks that use the most advanced technologies. The number of incidents and their complexity has grown exponentially in some cases. The difficulty of prosecuting these criminals and the existence of consistent business models have made this problem worse, without seeing the light at the end of the tunnel.
As if that were not enough, the situation has worsened, due to the lack of professionals with the training and skills necessary to defend the different components of our society - citizens, companies, governments, critical infrastructures, universities and research centers, armies and other security forces - in the face of these growing threats. There are different studies that address the problem of the lack of qualified people. As an example, it is interesting to review the study published in 2019 by the (ISC) 2, the “2019 (ISC) ² Cybersecurity Workforce Study”, which estimates the volume of additional professionals needed to face existing threats is more than four million. In the following graph, we can see the geographical distribution:
Source: 2019 (ISC)² Cybersecurity Workforce Study
Some voices within the industry are critical of these figures, claiming that professionals exist, although companies publish job advertisements with requirements that are impossible to meet, due to the high demand in both experience and knowledge of specific tools and cyber security solutions, many of them new to the market.
It is also true that we are at a time when the level of youth unemployment globally is simply shameful and unacceptable, including in the university segment.
Possibly, education and specialized training could be a solution to respond to both problems, employing young people and providing them with the cybersecurity training that the market requires.
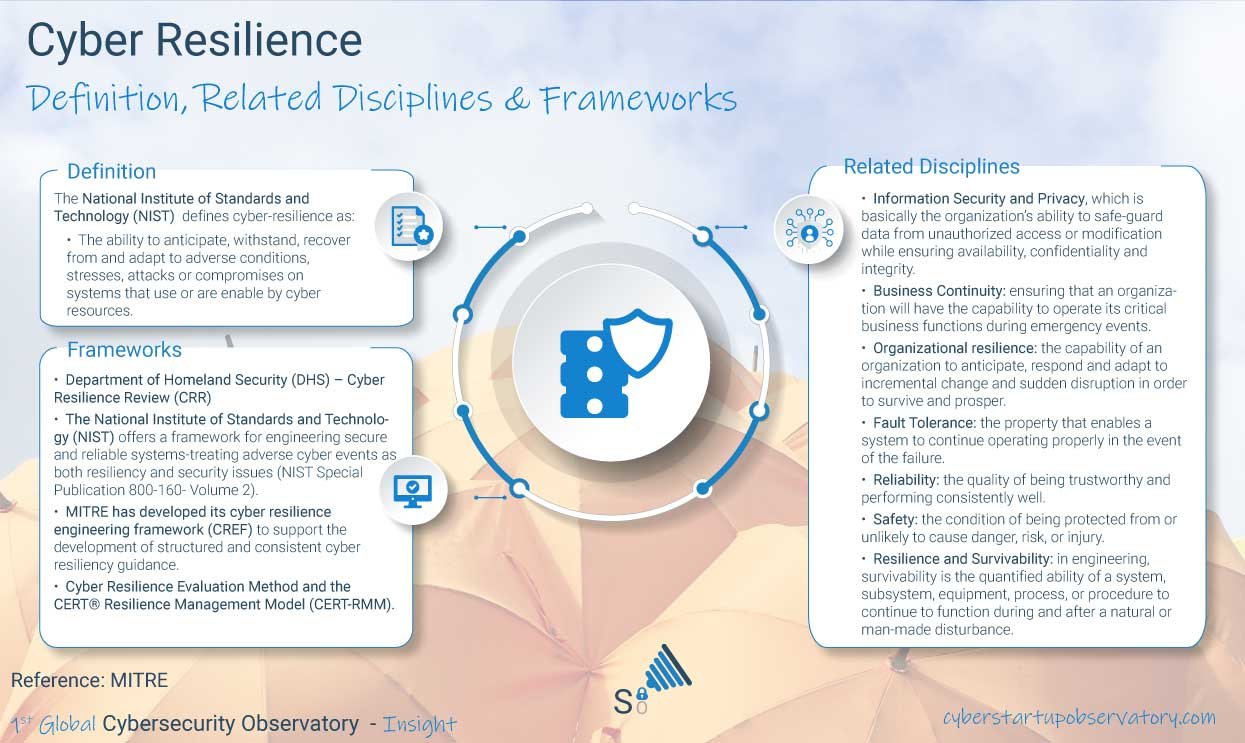
The different social actors dedicated to specialized security training play a key role, preparing our digital defense army. In the case of professionals from the SOC (Security Operations Center), CERTs (Computer Emergency Response Team), CSIRTs (Computer Security Incident Response Team), there is a solution that can play a key role in the training of professionals. This solution is the Cyber Range.
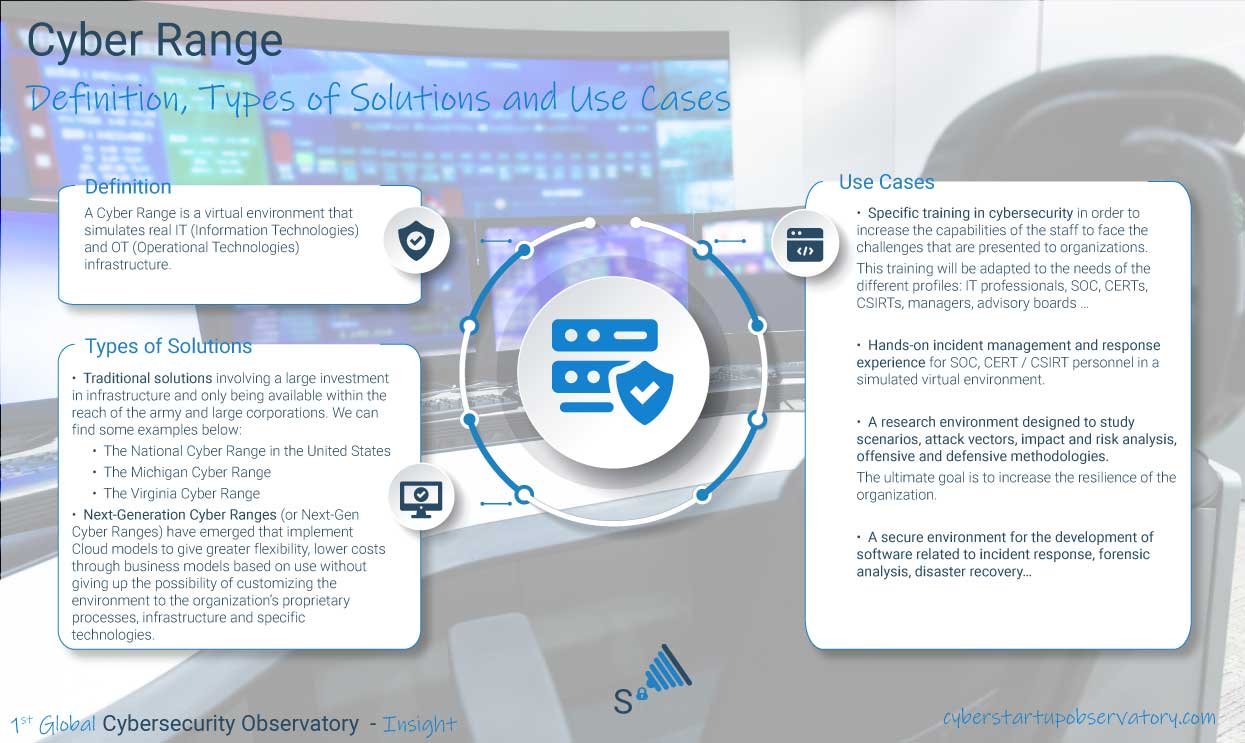
What is a Cyber Range?
A Cyber Range is a virtual environment that simulates real IT (Information Technologies) and OT (Operational Technologies) infrastructure, and is mainly used to carry out four key activities:
- Specific training in cybersecurity in order to increase the capabilities of the staff to face the challenges that are presented to organizations. This training will be adapted to the needs of the different profiles: IT professionals, SOC, CERTs, CSIRTs, managers, advisory boards …
- Hands-on incident management and response experience for SOC, CERT / CSIRT personnel in a simulated virtual environment.
- A research environment designed to study scenarios, attack vectors, impact and risk analysis, offensive and defensive methodologies. The ultimate goal is to increase the resilience of the organization.
- A secure environment for the development of software related to incident response, forensic analysis, disaster recovery …
Types of solutions and functionality provided
Traditional solutions involved a large investment in infrastructure, only being available within the reach of the army and large corporations. We can find some examples below:
- The National Cyber Range in the United States is a project supervised by DARPA to build a scale model of the Internet that can be used to carry out cyber war games. The project serves as a testing ground where the military can create antivirus technologies to protect against cyberterrorism and hacker attacks. Several organizations are involved in the development of the network, including Johns Hopkins University in Baltimore and Lockheed Martin. The Department of Defense has allocated more than $ 500 million to develop “cyber technologies.”
- The Michigan Cyber Range was established by the Merit Network in the summer of 2012 to teach cybersecurity certification courses and provide cybersecurity-related services.
- The Virginia Cyber Range is an educational and research institute funded by a $ 4 million grant from the Commonwealth of Virginia to promote cybersecurity education across the state.
However, in recent years, multiple solution providers called Next-Generation Cyber Ranges (or Next-Gen Cyber Ranges) have emerged that implement Cloud models to give greater flexibility, lower costs through business models based on use without giving up the possibility of customizing the environment to the organization’s proprietary processes, infrastructure and specific technologies.
These Next-Gen Cyber Ranges are specialized in training SOC professionals, providing them with a unique experience to carry out their daily work.
They allow, for example:
- Simulation of the customer’s IT infrastructure and architecture
- Simulation of current threats on modern IT and OT systems
- Anticipation of future threats to existing infrastructure
- Testing of new security solutions in a controlled environment
- And they enable the safe design and operation of Industrial Control Systems (ICS, for its acronym in English).
Cyber Range solutions you should know
ELTA establishes a Cyber Academy in the country, through high-level expert training solutions, which allow clients to obtain independent cyber knowledge to create their own Cyber Academy. Services include on-the-job and hands-on training, testing and operational support that will take your cyber team to an expert level.
Circadence Cyber Range-as-a-Service allows business, government and academic institutions the opportunity to train in realistic environments that reflect their real business networks. Its potential is limitless, with the ability to support the collective exercises of the Nation State as well as the modeling of entire cities to develop living physical and fifth domain environments.
This next-generation approach transforms traditional lecture-based learning, taking it outside of the classroom and into interactive real-world environments, at any scale, anytime, anywhere.
The main features are:
- Closed and virtualized network
- Emulation of interactive systems
- Real-time skills assessment
- Test, train and prepare cybersecurity teams
Quali Cyber Range on-Demand allows you to automatically configure and dismantle complex and isolated IT environments repeatedly as part of your cyber training and test solution. This solution is perfect for Red Team simulations - Blue Team: self-service secure environments for cyber ranks with one click. The key features of Quali’s solution are:
- The ability to create environments that authentically reproduce real-world environments, including physical infrastructure such as ICS and IoT.
- Model objects, including legacy protocols and devices, to create a realistic environment to support virtual pentest.
- Perform powerful automation and orchestration to address complex workflows and obtain exact replicas of production networks.
- Provide reservation and scheduling to avoid resource hoarding (physical or virtual).
- Reduce these environments in a time-limited manner to provide efficiency and support save and restore operations for analysis.
- Help train security, IT, and regulatory personnel on cybersecurity best practices, red-blue team exercises, drills and more with built-in LMS-like instructions.
- Governance, analytics and reporting along with self-service capabilities for multi-domain and role support.
Airbus Cyber Range is an advanced simulation solution that allows you to easily model IT / OT systems made up of dozens or hundreds of machines and simulate realistic scenarios, including real cyber attacks.
The Airbus Cyber Range is used by administrators, integrators, testers, trainers, and more to design virtualized or hybrid networks, emulate unit activities such as communications between two machines, or to launch complex scenarios that reproduce realistic activity (file sharing, email, web traffic and potentially real cyber attacks).
The CyberRange is available in a mobile box, in a bay or accessible from the cloud.
CDeX (Cyber Defense eXercise Platform) Cyber Range of specific training for cybersecurity, is a unique training system that helps increase the practical skills of specialists responsible for the security of the Telecom - IT infrastructure with respect to the detection and response to cyber attacks.
Training takes place in real time.
Training involves a Blue Team (a defensive team) and a Red Team (an offensive team).
The key technical characteristics are:
- Worldwide access to the platform 24 hours a day, 7 days a week
- Installation on premises (preparation in a maximum of 5 days) or in the cloud (in 30 minutes)
- Flexible and scalable work environment
Disclaimer
The Cybersecurity Observatory does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. The Cybersecurity Observatory research publications consist of the opinions of our own analysts and should not be construed as statements of fact.
No formal testing was performed on products or services for this analysis. These assessment findings are meant to serve as an input for our audience and their organizations. Users of these services must exercise judgement when choosing a service for their particular mission or telework needs.
We disclaim all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
All product names, logos, and brands are property of their respective owners. All company, product and service names used in this website are for identification purposes only.
Follow Us