Financial Cyber Drills
Author: Dr. Almerindo Graziano, CEO at Silensec | CYBER RANGES
Introduction
 Financial Cyber Drills - Cybercrime statistics concur that financial institutions have become the number one target of cyberattacks. Besides the immediate financial rewards, financial institutions are also custodians of a wealth of information about their customers, which once stolen can be re-sold and/or used to commit other cybercrimes, financially motivated or not.
Financial Cyber Drills - Cybercrime statistics concur that financial institutions have become the number one target of cyberattacks. Besides the immediate financial rewards, financial institutions are also custodians of a wealth of information about their customers, which once stolen can be re-sold and/or used to commit other cybercrimes, financially motivated or not.
Never like today must financial institutions be able to minimize the impact of cyberattacks, whether it is through the use of cyber threat intelligence, the development of advance detection and response capabilities, or the development of a strong security posture.
Regardless of the chosen solutions, the human talent component continues to play a pivotal role that many financial institutions struggle to address also because of the still increasing shortage of competent security professionals.

Attacks and security breaches have become the third unequivocal constant in every CISO’s life after death and taxes. CISOs have increasingly turned their attention to improving the cyber resilience of their organizations in order to minimize the impact and disruption of cyberattacks on their business. But how can CISOs assess their organizations’ cyber resilience?
In this paper, I analyze the different methods that financial institutions have at their disposal for assessing their cyber resilience, emphasizing the need for regular cyber exercises. I also elaborate on one specific type of cyber exercises, which we at Silensec have developed and call Cross Cyber Drills, which are proving – also with financial institutions – to be very effective in assessing cyber resilience beyond the resilience of systems (engineering approach) and encompassing people and processes. Finally, I put forward a number of guidelines to help financial institutions plan and execute effective cyber exercises.
Cyber Resilience
In recent years the term Cyber Resilience (or Cyber Resiliency) has gained great interest from CISOs from around the world. Such factors as remote working, digital transformation, ecosystem, supply chain risk management, cyber-physical convergence, cloud migration and shortage of competent workforce, increase the complexity of managing the security risk of the organization, especially when talking about large multinational financial institutions.
 While CISOs do not shy away from the security challenge, they have begun to look for new ways to validate how well their organizations will withstand an attack on their cyber infrastructures before those attacks occur. The term resilience has already been used for many years in different contexts[1], from National Security to Critical Infrastructures and more recently with reference to cyber security.
While CISOs do not shy away from the security challenge, they have begun to look for new ways to validate how well their organizations will withstand an attack on their cyber infrastructures before those attacks occur. The term resilience has already been used for many years in different contexts[1], from National Security to Critical Infrastructures and more recently with reference to cyber security.
NIST provides the following definition of Cyber Resilience (SP 800-160 Vol. 2):
“The ability to anticipate, withstand, recover from, and adapt to adverse conditions, stresses, attacks, or compromises on systems that use or are enabled by cyber resources.”
On the other hand, Gartner defines organizational resilience as “the ability of an organization to resist, absorb, recover and adapt to business disruption in an ever-changing and increasingly complex environment to enable it to deliver its objectives, and rebound and prosper” (a slightly modified version of the ISO 22136:2017 definition).

Regardless of the actual definitions, everyone can agree that cyber resilience addresses organizations as a whole and it is not just a matter of security posture and security controls being in place. Also, the underlying message within the term cyber resilience is about the growing reliance of organizations and society as a whole on cyber resources, a reliance that is only going to grow deeper and wider with the increasing adoption of cyber-physical systems.
At a high-level, a cyber resilient organization must be able to:
- Anticipate Attacks – This ability is often related to the development of threat intelligence capabilities and the associated capability of the same organization to create plans and deploy security controls to minimize the risks of impending threats (e.g., by addressing the targeted vulnerabilities).
- Withstand Attacks – Despite the best effort and good security posture, attacks will still manage to get through the organization’s defences and sometimes they stay resident as in the case of APTs. The ability of an organization to withstand an attack is linked to its monitoring and detection capabilities and to the effectiveness of the overall incident response process.
Obviously, an organization must also continuously improve and learn lessons from experience and from reflecting on it. As Sir Winston Churchill quoted:
“All men make mistakes, but only wise men learn from their mistakes.”
However, more recently, Warren E Buffett, an American business magnate, philanthropist, and one of the most successful investors in the world (CEO and Chairman of the Omaha-based multinational conglomerate company Berkshire Hathaway), better articulated it as follows:
“It’s good to learn from your mistakes. It’s better to learn from other people’s mistakes.”
In the financial sector, a pivotal publication recognizing the importance of cyber resilience is the CPMI-IOSCO guidance on cyber resilience for Financial Market Infrastructures (FMIs), published in June 2016[2]. In this document, the authors call for FMI to establish a comprehensive cyber resilience framework that includes a testing programme to validate its effectiveness. Specifically, understanding (through testing) the overall effectiveness of the cyber resilience framework in the FMI and its environment is essential in determining the residual cyber risk to the FMI’s operations, assets, and ecosystem. Such testing must simulate tactics, techniques and procedures (TTPs) of current and relevant cyberattackers as gathered from threat intelligence.
Assessing Cyber Resilience
 While many CISOs focus on improving the cyber resilience of their organizations, the testing and assessment of such cyber resilience remains an integral part of the overall digital risk management strategy.
While many CISOs focus on improving the cyber resilience of their organizations, the testing and assessment of such cyber resilience remains an integral part of the overall digital risk management strategy.
International best-practice security standards, such as ISO 27001, require organizations to plan and execute regular audits every year. Similarly, organizations should develop annual programmes to test their cyber resilience regularly and to use the outcomes of those assessment for improving their cyber resilience.
Most importantly, the assessment of cyber resilience should include internal and external stakeholders playing different roles within the organizations, including senior management, operational personnel, regulators, ecosystem partners, and financial authorities.
Today, CISOs wishing to assess the cyber resilience of their organizations use, or are looking to apply, one of the following methods (please bear in mind that not every method is appropriate for assessing cyber resilience and some are more appropriate than others):
Breach and Attack Simulation (BAS)
Breach & Attack Simulation (BAS) tools and solutions have become widely popular in the industry in recent years. Attack simulation refers to the ability to simulate a threat actor’s tactics, techniques and procedures (TTPs).
The business focus of most attack simulation tools and platforms is to provide a (semi) automated means of obtaining the attacker’s view or perspective of the target organization. While traditional vulnerability scanning technology focuses on the identification of systems, networks and application vulnerabilities, BAS solutions go the extra mile by allowing to simulate the different phases of the security kill-chain, while at the same time providing recommendations on how to secure the organization.
Sample features of BAS solutions include:
- Agent-based install on the production environments
- Provide an automated attacker’s view of an organization’s environment
- Provide recommendations to mitigate gaps
- Map assessment findings to MITRE ATT&CK.
BAS solutions are fundamentally audit solutions to understand the organization’s exposure to cyberattacks across the entire cyberattack surface, helping the organization to prioritize risk mitigation strategies and improve its security posture. In that respect, BAS solutions help by increasing the ability to anticipate and withstands attacks.

However, when it comes to assessing an organization’s cyber resilience, BAS solutions have the following shortfalls:
- BAS solutions only simulate attacks – BAS solutions are deployed on production systems. As such they limit themselves to only simulating the attacks. For instance, when simulating a ransomware attack, the files that the BAS agent tries to write on disk in the production systems are harmless files, which simply contain hashes of known malicious entities. This way, a SIEM might flag such files if they are even allowed to be written, while endpoint security controls deployed on the machines might quarantine the actual files. From a cyber resilience perspective, BAS will help organizations identify configuration gaps and help improve the security posture of the organization but it will not address the human factor side of the resilience, leaving the CISO wondering “what if…” with no strong assurance or confidence.
- BAS solutions only address the system side of the organizational resilience – Cyber resilience includes the ability of the organization to detect, respond and mitigate the impact of attacks affecting the cyber resources of the organization. In other words, a cyber resilient organization will have mature and effective processes and competent staff in place in order to be able to detect attacks that have slipped through the hardened net of security controls - it will then be able to respond to such attacks in order to minimize their impact on the business.
BAS solutions are here to stay and to become a permanent solution for CISOs of all organizations. However, they only address the system aspects of the cyber resilience, leaving aside the human components of talent and security processes.
Red Team Simulation
 A Red Team Simulation is an engagement where the tactics, techniques and procedures (TTPS) of real-life attackers are simulated on real production environments in order to reveal the strengths and weaknesses of the organization being tested, enabling it to reach a higher level of cyber maturity.
A Red Team Simulation is an engagement where the tactics, techniques and procedures (TTPS) of real-life attackers are simulated on real production environments in order to reveal the strengths and weaknesses of the organization being tested, enabling it to reach a higher level of cyber maturity.
Red Team Simulations are tailored to an individual organization to simulate an attack on the critical functions of that organization and its underlying systems (i.e., its people, processes and technologies).
Several Red Team Testing frameworks have been developed around the world. Notable examples include:
- The European Union Threat Intelligence-Based Ethical Red Teaming framework (TIBER-EU)[3]
- The CBEST framework in the United Kingdom, developed by the Bank of England[4]
- The Intelligence-led Cyber Attack Simulation Testing (iCAST) by the Hong Kong Monetary Authority (“HKMA”)
- The Financial Entities Ethical Red-Teaming (FEER)[5] by the Saudi Arabian Monetary Authority
- The Adversarial Attack Simulation Exercises (AASE)[6] developed by the Associations of Banks in Singapore.
The figure below illustrates a typical process for the execution of Red Team Testing, from procurement, scoping up to execution, according to TIBER-EU:
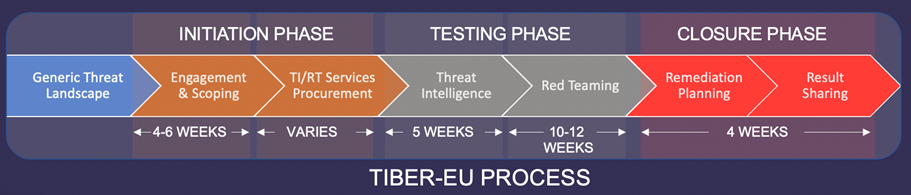
Other frameworks provide a similar structure. Overall, the following considerations can be made with regard to Red Team Testing and cyber resilience assessment:
- Costly Engagement – A red Team Testing exercise is a multi-stakeholder engagement carried out on production environments. As such it requires considerable planning and resources.
- Long process not suitable for many iterations – Due to its nature, a Red Team Testing engagement is usually a once-a-year activity at best. In reality, many financial institutions do not even carry them out annually.
- Organizations have to wait for the next iteration to assess any applied improvements.
- It is delivered on production systems – Because of the live production systems being targeted, Red Team Testing engagements have to somewhat limit the realism of the attack simulation in order to limit the risk of unforeseen negative impact on the business.
Cyberdrills
A cyberdrill is a planned event during which an organization simulates cyberattacks, information security incidents or other types of disruption to test the organization’s cyber capabilities, from being able to detect a security incident to the ability to respond to it appropriately and minimize the impact on the organization’s business.
Such simulations are captured into what is normally called a scenario, which includes a storyline, a simulated environment, some challenges and much more, depending on the scenario. Overall, cyberdrill scenarios fall under one of the following two types:
- Table-top (TTX) – These are discussion-based scenarios, where participants usually role play to simulate their reactions in real-life situations. During TTX exercises, a facilitator guides participants through a series of “injections”, i.e., fictitious events such as, for instance, receiving a threatening email or the news of a critical vulnerability or a declaration by a hacktivist group. TTX are best suited for testing security processes.
- Operational (Hands-on) – In these exercises participants are required to interact with simulated systems and test their ability to carry out typical cybersecurity tasks such as identifying and responding to a security incident, performing malware analysis, carry out some computer forensics etc.
Table-top exercises
Table-top exercises are great - they will always play an important role in the CISO tool chest but they have the following shortcomings:
- TTXs are not inclusive – In the majority of cases, TTXs only involve the management side of the organization and not its technical side. When they do involve operational staff, TTX are simply simulating threats to elicit responses from the audience and to validate the decision-making processes. For instance, when simulating ransomware the TTX may require the SOC team to choose from a list of available options or to suggest alternative actions. In no case will anyone be required to perform an activity of malware analysis or log analysis or any other practical activity
- Processes and not Operations – TTX are a great way of testing the knowledge and understanding of processes, but they fall short in the validation of the process execution since everything is simulated with little to no operational engagement.
As an example, a TTX may help validate if an organization’s incident response process is sound and if it has been developed according to best practice. It may even help validate to what extend staff follow the process.
Operational Exercises
Operational exercises have been run successfully for many years across many different business sectors. However, Operational Exercises come with the following shortfalls:
- Operational Exercises are not Inclusive – Just like TTXs were not inclusive of the operational staff, Operational Exercises are not inclusive of the management roles. Responding to security incidents requires sound technical competencies but it also impacts on the business and thus it requires communication, escalation, and coordination with other entities, involving Management up to the Board to take important decisions which can affect the execution the of the incident response process.
- Lack of Business Context – Operation exercises tend to focus on the technical side to assess the abilities of the operational staff in dealing with specific phases of the incident management process or across the entire lifecycle of a security incident. Yet the focus is on “can you do it” and “can you fix it” type of questions rather than “do you understand the impact this has on the overall organization” and “are you able to effectively collaborate and communicate with non-technical staff” to minimize the impact of the security incident to the business.
While traditional cyberdrills fail to capture the communication and collaboration aspects within an organization and between different organizations, C2 Drill scenarios are designed to include both table-top and hands-on exercises simultaneously, allowing the participants with different roles and responsibilities to interact with one another, simulating the entire business and its operational relations within the organization and its ecosystem, as and if involved.
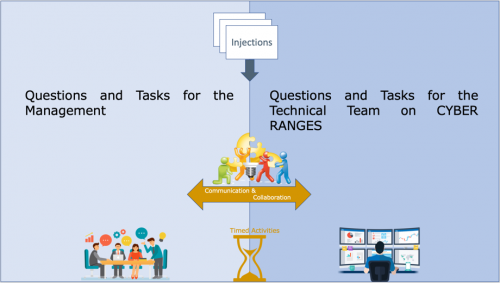
C2 Drill Apporach
The following figure illustrates the typical delivery plan for each scenario in a C2 Drill.
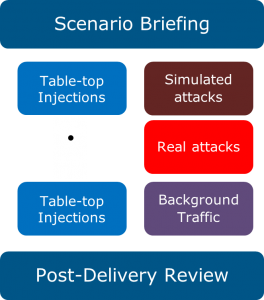
Scenario Delivery Format
Participants are divided into two groups. Group one includes all the participants involved in the technical hands-on exercises. Group 2 includes the management involved in the table-top simulations.Each scenario begins with a briefing session to introduce it, its objectives and to explain the rules of engagement. Information about the simulation environment and how to access it is also provided in order to ensure all participants are ready to begin the cyberdrill.
Each scenario is designed to require hands-on responses and activities with, at the same time, management reflections, discussions and decision points. Furthermore, each scenario requires the two different groups to interact with one another at different stages, simulating the typical interactions and communications of a real-life scenario.
Planning a Cross Cyber Drill

Whether it is a TTX, an Operational Exercise or a Cross Cyber Drill, the truth is that cyber exercises should be taken on a regular basis and more than once a year. Unfortunately, the main reason why this does not happen is costs! The high costs are explained by the customization of the exercise for the target organization. Let’s take ransomware as an example. A generic TTX on ransomware will have little to no value to an organization of a certain maturity level. A more mature organization will most likely require the TTX to be customized to take into account the organization’s security processes, incident response playbooks, organizational structures and more. All this drives the costs up. Then again, once run, the TTX loses its value. Similar considerations can be made for other types of exercises.
Other reasons affecting the regular execution of cyber exercises include:
- Lack of Established Assessment Frameworks and Methodologies – Unlike Red Team Testing Frameworks, cyber exercise frameworks are less established. Cyber exercises in the commercial sector are less mature in that respect. Organizing a cyber exercise, especially involving many stakeholders is not an easy task and the delivery of the exercises often leaves the organizations wanting.
- Maturity of tools and technology – Automation means lower costs, greater speed of execution and increased realism. Most tools and technologies used in cyber exercises today lack automation and are heavily dependent on security professionals and facilitators to run the show on stage and at the back. Setting up and maintaining simulation environments is still expensive.
- Maturity of assessment frameworks – Everyone wants the assessments to identify the gaps and shortfalls that need addressing. However, there is no click-and-run type of cyber exercises, and there is no click-and-run type of assessments that will just observe the actions and responses of the people participating in the cyber exercise and spit out the organization’s scorecard. At least not just yet.
Much of the costs associated with the regular assessment of cyber resilience are related to the inability to automate the tasks and activities that can and should be automated, such as for instance:
- Management Workflow of Simulation Environments
- Attack Simulation/Emulation
- Management of interactions amongst multiple stakeholders (e.g., management and technical staff).
What is a Next-Generation Cyber Range?
When talking about cyber ranges and trying to understand the difference between traditional, old-generation cyber ranges and next-generation cyber ranges, the key point is about the ability of a cyber range to address both the aspects of scaling the exercise and the experiential learning methods applied in a manner that is cost-effective for the organization.
Next-generation cyber ranges address both scale and method, simultaneously. Next-generation cyber ranges come with the following characteristics:
- High orchestration to scale both skills development and application of such skills in realistic simulation environments
- Integrated functionalities to support different use cases
- User Activity and Attack Simulation/Emulation
- Ability to easily add experiential learning content for both the development of skills and the application of such skills in realistic deep-dive simulation environments
- Ability to be deployed on cloud or on premises with comparable costs
- Click-and-play ease of use even for complex high-fidelity simulation environments
- Integrated learning management system to manage users’ upskilling progression and experience.
The following figure illustrates the architectural components of a next-generation cyber range. Compared to traditional ones, next-generation cyber ranges integrate multiple functional components, on top of the traditional ICT/OT simulation, to provide the end user with automated functionalities, which heavily reduce the resource requirements to execute cyber drills and to simulate and denotate attacks, providing users with a practical and effective one-click experience.

Using a Next-Generation Cyber Range for Improving Cyber Drill Automation
Since every organization is different, assessing cyber resilience will never be a fully automated process. However, there is light at the end of the tunnel that is bound to change this limitation for the entire financial sector and other industries alike.
Many organizations are beginning to look at next-generation cyber ranges to heavily cut down on the costs of execution of cyber exercises and to integrate both TTX and Operational Exercises into a single platform for a comprehensive end-to-end assessment of cyber resilience.
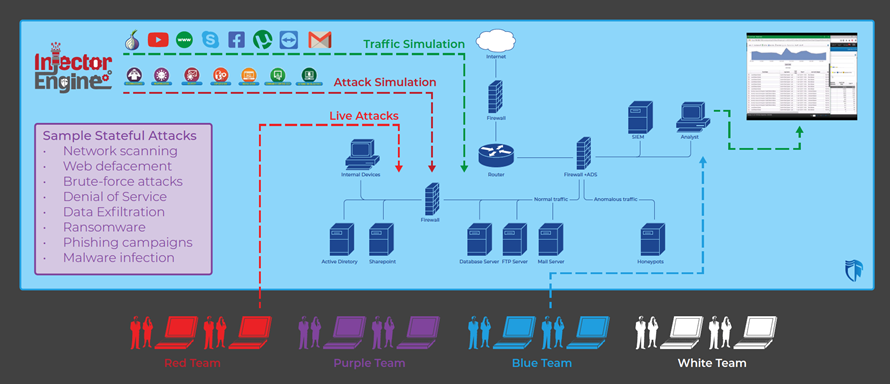
Cross Cyber Drill on CYBER RANGES – a simplified setting
Assessing cyber resilience with a next-generation cyber range includes the following steps:
- Development of Replica Environments – The replica environment must be representative of the organization’s infrastructure, including the same security controls and infrastructure assets in order to facilitate a confident appreciation of the organization’s response to the attack simulation. The set-up of the replica environment should also be based on the analysis of the organization’s security processes, incident response playbooks and reflect the security maturity of the organization.
- Development of attack simulations based on threat intelligence – Once the replica environment has been set up, attack simulations can be developed on the basis of current and relevant threat intelligence.
- Click-and-play execution of threat simulations – In this phase, the environment is ready to be used for fast execution and against limited resources to test and evaluate the cyber resilience of the organization.
- Semi-Automatic capture of actions and responses – Stakeholders’ interaction is captured and observations documented by the facilitators of the cyber exercise.
- Value-Added Reporting on Cyber Resilience – A report is produced capturing the level of cyber resilience, mapping the organizational response to specific cyberattacks.
Naturally, the above process relies heavily on two aspects:
- The use a of next-generation cyber range
- The use and integration of a cyber resilience assessment framework, which the cyber range will help automate to the extent possible, leaving the “humans” in charge of the tasks of planning and executing the exercise, and analyzing its results in terms of cyber resilience assessment.
The current maturity of some next-generation cyber ranges, such as CYBER RANGES by Silensec, has already reached a level that allows financial institutions to comfortably deploy them for the running of Cross Cyber Drills.
The cyber resilience assessment frameworks, in relation to the use of cyber ranges, are still maturing but are expected to reach maturity in the near future, as more and more organizations begin to use a next-generation cyber range for comprehensive exercises and to contribute to the development of best practice.
Conclusions
Financial Cyber Drills - Financial institutions should begin to look at alternative methods of assessing cyber resilience, which require lower costs and allow for more frequent execution and comprehensive deep-dive test activities. Specifically, organizations should consider the adoption of Cross Cyber Drills, powered by a next-generation cyber range to improve the automation of exercises, reduce their costs and integrate the regular assessment of their cyber resilience into the organization’s digital risk management strategy.
 Dr. Almerindo Graziano, CEO at Silensec | CYBER RANGES
Dr. Almerindo Graziano, CEO at Silensec | CYBER RANGES
Dr. Al Graziano founded Silensec in Sheffield (UK) in 2006, after a successful career as the university course designer and then director of the first UK MSc. Information Security programme. An ISO 27001 certified cyber security solution provider, Silensec has been delivering hands-on cyber drills to national CERT/CSIRT since 2014 in collaboration with the UN’s International Telecommunication Union.
Silensec has developed the latest ITU Cyber Drill Framework. CYBER RANGES by Silensec is the only next-gen cyber range platform with its full feature set available on premises, on private and public cloud, and portable.
Silensec is a member of the European Cyber Security Organization (ECSO) and co-chairs the ECSO Working Group WG 5 on cyber ranges, cyber exercises and training, and also at sub-WG 5.1 (cyber ranges) and sub-WG 5.2 (education and training), furthering the best practice in the area of cyber ranges and cyber exercises.
Silensec is also a Premium Partner of the Global Cyber Alliance (GCA), based in New York, London and Brussels and focused on cooperation between industries and governments in tackling cybercrime.
References:
[1] MITRE Cyber Resiliency FAQ https://www.mitre.org/sites/default/files/PR_17-1434.pdf
[2] (2016) Guidance on cyber resilience for financial market infrastructures, https://www.bis.org/cpmi/publ/d146.pdf
[3] European Central Bank (2018). TIBER-EU FRAMEWORK https://www.ecb.europa.eu/pub/pdf/other/ecb.tiber_eu_framework.en.pdf
[4] Bank of England (2021). CBEST Threat Intelligence-Led Assessments. https://www.bankofengland.co.uk/-/media/boe/files/financial-stability/financial-sector-continuity/cbest-implementation-guide.pdf
[5] Saudi Arabian Monetary Authority (2019). Financial Entities Ethical Red-Teaming. https://www.sama.gov.sa/ar-sa/Laws/BankingRules/Financial_Entities_Ethical_Red_Teaming_Framework-AR.pdf
[6] The Associations of Banks in Singapore (ABS)(2018). Red Team: Adversarial Attack Simulation Exercises. https://abs.org.sg/docs/library/abs-red-team-adversarial-attack-simulation-exercises-guidelines-v1-06766a69f299c69658b7dff00006ed795.pdf
Follow Us
Financial Cyber Drills

