Next-gen Cyber Ranges: delivering customer-specific repeatable large-scale realistic exercises
Authors: Dr. Al Graziano, CEO / Marcello Hinxman-Allegri CMktr SCIP, Head of Marketing & Business Development, Silensec | CYBER RANGES
 Introduction
Introduction
Next-gen Cyber Ranges: delivering customer-specific repeatable large-scale realistic exercises.
Gartner has predicted the use of cyber ranges by large organizations to rise from 1% to 15% by 2022. Cyber ranging is an increasingly well appreciated way of boosting cyber dexterity, cyber posture and resilience for nations and organizations alike, since cyber ranging effectively addresses the 3 dimensions of cyber security: people, processes and technologies.
This translates into the following number of macro use-cases:
- research/testing/analysis,
- training and learning,
- compliance,
- assessment of people/processes/technologies,
- proof of concept.
As people are considered the ultimate human firewall against cyber threats, training has been given great consideration. Traditional approaches to cybersecurity training are focused on skills transfer against given subject areas. They lead to degrees and qualifications: there is a big market with huge demand and supply, but the worldwide number of jobs to be filled still greatly exceeds the number of candidates.

Also, there is mounting doubt among employers whether such candidates, whether graduated and/or certified, are really fit for the job and able to hit the ground running. In some countries, such as those in the FVEY group, there are extensive re-skilling programmes under STEM education, to support the transition of active service men and women to civilian roles.
It is easy to get entangled in the intellectual discussion, as old as the e-learning revolution, about competencies, curricula and syllabi. From our many conversations with corporate and government clients, it seems very clear that we should care about two questions:
- do deep-dive experiences better prepare organizations to respond when facing an incident?
- equally importantly – can that be proven? And how?
A further element of concern for close consideration is about the actual mix of hard vs. soft skills, and that of knowledge, skills and abilities. We have had great discussions in the USA about this: how do we secure that the cross-departmental Cyber Security Force of our organization can deal with an incident or a cyber threat in a both timely and effective manner? Coordination and collaboration attitudes and processes are as valuable as technical hands-on defense or counter-defense capabilities and viceversa. Technical capability though lags behind.
 Also, tracking and monitoring the human cyber capabilities in our technical teams is vital to the understanding of our risks and how to mitigate them. Evidence of expertise is something more than just in-depth performance metrics to help an organization identify and act on areas of potential or actual or residual risk.
Also, tracking and monitoring the human cyber capabilities in our technical teams is vital to the understanding of our risks and how to mitigate them. Evidence of expertise is something more than just in-depth performance metrics to help an organization identify and act on areas of potential or actual or residual risk.
Residual risk is what eventually determines the degree of an organization’s resilience. The very concept of resilience is also very important: it is no longer about whether we get hit in cyber, but when and, when that happens, shall we be able to stand and recover? And how fast and well, too?
And as “no man is an island” in cyber, teamwork considerations need making: even a medieval knight with his (or her) shiny armour used to rely on servants, squires, foot soldiers, spare horses and equipment. There is no cyber security professional in fact working alone, whether partaking an internal/extended incident response team or a company’s CISO being supported by an external MSSP, or an organization with its industry CSIRT.
Practice beyond training means exercising. A cliff climber can practise on real rocky ground or on a climbing wall, in or outdoors. But if a mountaineer aims to the top of Mount Everest, he or she will rely on an expedition team. Similarly, an army platoon or a SWAT team will learn, train and practise in artificial vs. real settings, even under fire with an established degree of safeguards.
Obviously, every government or industry sector has got specific needs for realism, whether in a vanilla or true-to-life setting (depending on the use case) and with the involvement of other individuals, the whole team or organization, partners’ ecosystem, and the wider public.
Practice through highly realistic exercises often implies one-off experiences due to the high costs of implementation, the pre-requisite rules to be applied (as when pen-testing by ethical hackers), and other operational constraints to be imposed on the live production infrastructure for safety and security purposes. Try think of a breach-and-attack simulation on a live infrastructure to ring-fence versus a highly-gamified live-fire simulation on such a next-generation platform as CYBER RANGES.
Undoubtedly, the larger and more articulated the exercise setting is up to a full-blown live environment, the further away the results and value of the exercise are from the mere application of knowledge and skills as in a training exercise.
Exercises can be of various formats, such as table-top, technical (or cyber), cross cyber, war games, CTFs, and more. They aim to provide opportunities for organisations to demonstrate critical capabilities and reveal how effectively they integrate people, processes, and technology to protect their critical information, services, and assets. The text box provides a sample of exercise definitions:

“Understanding Cyber Ranges: From Hype to Reality” (ECSO WG5, March 2020)
In a true-to-life cyber security simulation exercise, which may typically involve both technical and non-technical people (we at CYBER RANGES refer to this format as a Cross Cyber eXercise or C2X), senior cybersecurity and IT/OT leaders, together with peers from other departments (e.g., Legal, Marketing, Customer Service), can work to identify the roles and responsibilities of managing cybersecurity incidents and the technical and operational processes needed to detect and recover from cyber-attacks with the hoped-for business continuity.
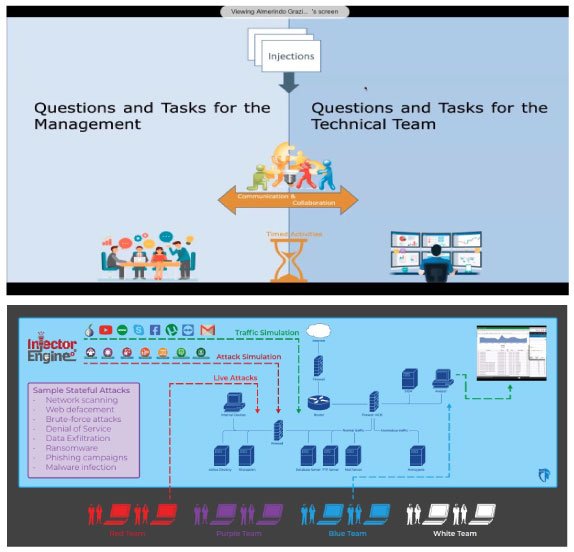
Cross Cyber eXercise on CYBER RANGES – a simplified setting
A cyber security exercise worth the time spent on it, comes with specific objectives:
- Establish the KPI of the exercise against the chosen use case.
- Identify key participants who would lead the company or companies during a cyber-attack
- Bring organizations together, individually, along the value chain and sector-wide, in a unified way to build industry response and recovery capabilities and identify participants’ roles and responsibilities.
- Test operational resiliency key concepts across the organisation/s
- Provide recommendations and advice on best practices in detecting, responding to and recovering from cyber-attacks
- Improve coordination and information sharing across the sector around detecting, responding to, and recovering from cyber-attacks
In March 2021 we facilitated a C2X with participants from 15 European banks, of SOC analyst to HR/Audit/Regulatory Affairs/CISO role and grouped into ten teams: that C2X witnessed how senior managers very much cherished the opportunity to work side by side with their cyber operations colleagues and how they could gain a fuller rounder understanding of the cyber security climate they actually work in. Here is a statement:
“The idea of exercising incident response is great and useful: it should be repeated more often. Sharing the advice and the discussion were very useful. (…) For some of us who are not working on technical on a daily basis, this [exercise] is good for practice. (…) Well organized, thank You. It was a thrilling event.”
The Exercise Methodology
When using a realistic and pertinent cyber-attack scenario, participants will be asked to register on some virtual platform on which to exercise against that cyber-attack. There is a variety of exercise platforms out there to handle the expected interaction between participants and scenarios, with the more advanced platforms, i.e. cyber ranges, providing a deep-dive engaging gamified experience of interfacing with the cyber-attack simulation.

According to ECSO (Mar-2020) “it is important to understand that, in order to fully meet the specific requirements of the use case, a cyber range must possess or expose specific functionalities and/or capabilities (…) Cyber ranges can be used by a wide range of target users. However, not every cyber range is open or meant to be used by every category of users”.
This is a list of target users and target entities for cyber ranges:
- Corporate (private and government)
- Strategic decision-makers (private and government)
- Security professionals
- Military agencies and Computer Network Operations (CNOs)
- Security Operation Centres (SOCs)
- Educators
- Students
- Researchers
- Event organizers.
Scenarios may not be technical, thus better suited to executive decision-makers. Parts of the exercise will be about watching cyber attacks unfold, while other participants will deal with the response to challenges, questions and scenarios applying the tools-of-trade they have at work. Participants will be expected to play themselves or assigned roles, and to propose solutions based on their assigned plans, policies, systems and procedures.
As cyber readiness is not just about testing technical teams, it is also about exercising how security leaders and senior managers make decisions in the heat of a cyber crisis. The best kind of exercises are dynamic, alternating outcomes to show the impact of decisions made under pressure.
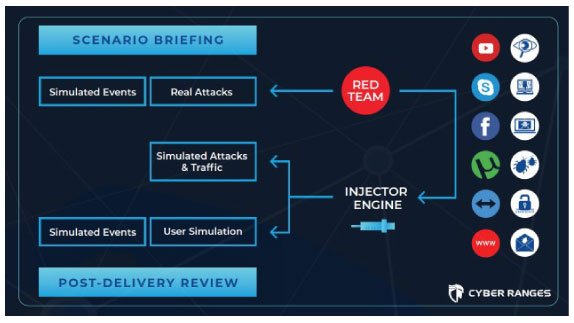
CYBER RANGE - Structure of Cyber Security Exercise
Scenarios can be combined together to achieve the goals of an exercise. Sometimes they are built very sophisticatedly to use an organization’s infrastructure replica, and to offer participants the chance to perform live-fire exercises, a.k.a. blue vs. red teaming.
Traditional red teaming is usually led by seasoned security professionals and staged under controlled environments. While red and blue team exercises have long been an important security tool, they present with two key disadvantages: they are 1) highly manual and 2) resource intensive. This means that most organizations can only run these tests only now and again, and that, during the weeks or months between tests, vulnerabilities may arise undetected and defenders have little visibility into the true state of their security environment.
Nowadays, red team activity is often carried out with various degrees of automation and realism with or without human involvement. In fact, with more advanced exercise platforms, such as next-gen cyber ranges, agent-based technology enables the injection of real use traffic and attack vectors, even very complex APTs as from the MITRE ATT@CK Matrix or custom-built. Injections can be scheduled or on-demand, controlled by the scenario itself or by an instructor leading on the exercise.
The availability of an Injector Engine (see the CYBER RANGES diagramme above) also makes it easier to repeat complex scenarios, even with large groups of participants, over time and in a secure environment. This avoids the constraints and costs of such approaches as breach-and-attack (even with traffic generators) or live red teaming.
An example of large-scale exercise was the ITU 2020 Global Cyber Drill, based on multiple simulation scenarios (six over 6 days) with 247 participants from national CERTs and CSIRTs of 57 countries. CYBER RANGES by Silensec powered the ITU 2020 Global Cyber Drill. Because of COVID-19 it was held online in safe mode. Such a delivery option was unheard of with old-generation or less sophisticated cyber ranges.
The ITU 2020 GCD planners scoped the exercise to focus on the challenges around the healthcare sector eco-system, building the challenges upon real-life inspired use-cases. The aim was to engage the CIRT community with realistic serious gaming, challenging their skills and knowledge while building competence around technical incident analysis, network and system forensics, lateral movement, OT challenges and live red teaming, coordination and collaboration among CIRTs.
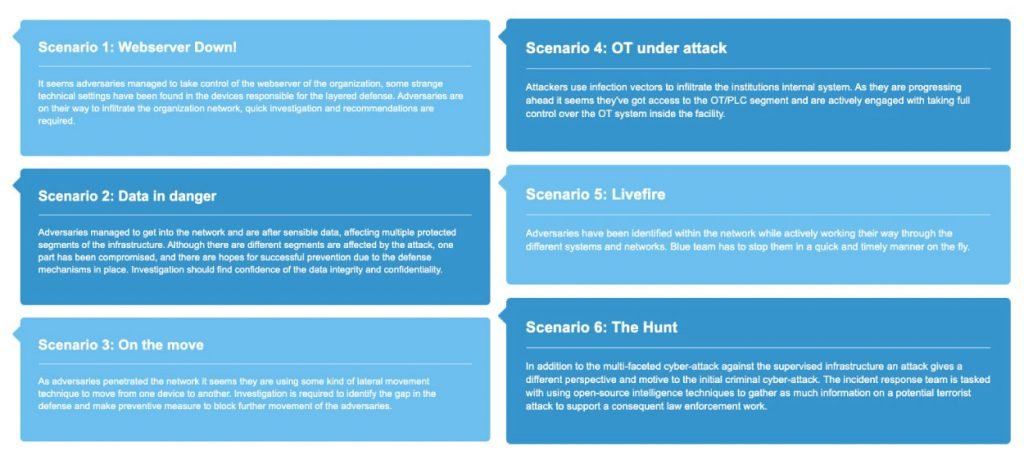
ITU 2020 Global Cyber Drill powered by CYBER RANGES (source: www.itu.int)
By the way, as reality always beats fiction, soon after the ITU 2020 GCD an actual cyber-attack hitting the European Medicines Agency (EMA) was reported in the news!
Exercises and cyber ranges
Depending on the intended use of the cyber range, certain functionalities can be considered desirable or even de facto mandatory. Where those functionalities are not natively supported by a cyber range, systems and applications from third parties would need integrating with the cyber range. In such cases, one must carefully evaluate and address the integration and compatibility challenges that would arise.
A key characteristic of a next-generation cyber range is its full-lifecycle content platform nature beyond the simulator features, in particular as regards the management of users and scenarios for running exercises.
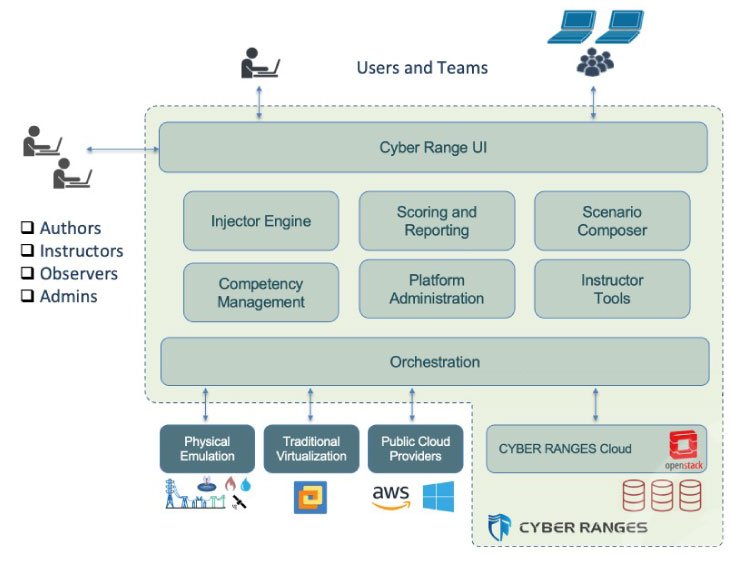
Next-Gen Architecture: CYBER RANGES by Silensec
A large-scale exercise, involving a very large number of virtual machines (VMs), regardless of the use case, has a de-facto requirement for orchestration. At its finest, orchestration may be used to automate tasks and interactions across different components of the cyber range, such as the ability to schedule attacks and user simulation, events injection to initiate the collection of user activities and more, depending on the specific use cases.
Orchestration and cloud technology
 Cyber range orchestration greatly affects the scalability, usability and cost of using a cyber range as well as the support for specific use cases, such as the ability to automatically schedule attacks and user activity simulation, events injection and more. Orchestration is a crucial functionality.
Cyber range orchestration greatly affects the scalability, usability and cost of using a cyber range as well as the support for specific use cases, such as the ability to automatically schedule attacks and user activity simulation, events injection and more. Orchestration is a crucial functionality.
The widespread adoption of the word ‘cloud’ (with its alas improper use) has confused matters when it comes to cyber ranges. A cloud cyber range is a cyber range available through the cloud, normally a public one. A cloud-based cyber range is instead a cyber range built on cloud technology, which does not necessarily mean that the range is available through the cloud, although that is also likely. The key here is to focus on the underlying technology used for the development of the range.
Cloud-technology is the key technology that can effectively address the scale aspect of the security training. While building on conventional virtualization, cloud virtualization abstracts the underlying physical resources across an entire infrastructure and makes them available transparently to end users.
A cyber range with orchestration capabilities can support additional functionalities, which would otherwise require additional manual effort and coordination and hence additional costs for running an exercise.
The inherent support for dynamic configurations, increased efficiency and scalability required to run large-scale exercises makes cloud technology a natural choice of implementation for modern cyber ranges, although not for all cyber-range use cases and not necessarily across the different types of cyber-range users.
Authoring scenarios for meaningful exercises
The ability of a cyber range to support the delivery of effective exercises relies on its ability to support the development of scenarios whether by the vendor, the users or even third parties. The opportunity of attracting contributions from subject matter experts and from up-to-date intel or other research and that of addressing custom specs requirements for infrastructure replicas, integration of technologies, incl. OT/ICS/IoT, new vulnerabilities and novel attack vectors greatly enhance the usefulness and value added of a cyber range.
Some cyber ranges have equipped themselves with clever scenario composition tools, which can include anything from the ability to create basic simulation environments up to full-scale custom simulation of attacks and other services.
The aforementioned ITU 2020 Global Cyber Drill could benefit of the CYBER RANGES Scenario Composer and Injector Engine for the development of its 6 scenarios by 6 authoring teams, incl. our own team, another range vendor, a European university and the UN Counter Terrorist Office.
Building realism into exercises
To guarantee that an exercise offers participants a truly engaging and realistic experience, there are some crucial fundamentals to provide:

- Simulation of Internet services – modern cyber-attacks are disguised to avoid detection. It is very important for a cyber range to be able to simulate the Internet and its services in a realistic way, incl. Facebook, LinkedIn, Twitter, app stores, Internet routing protocols and different tiers of service providers, controlled update and software repositories, global services such as name resolution, PKI, PGP, public news sites and discussion fora and up to the Dark Web and TOR networks.
- Attack simulation – this domain is growing, but most attack simulation tools and platforms are focused on the (semi) automatic testing of the corporate security posture, mainly breach and attack simulation. More recently, breach and attack simulation has been increasingly focusing on the MITRE ATT&CK® knowledge base of adversary tactics and techniques, moving away from the traditional security kill-chain model. In many cases, attack simulation in cyber ranges is limited to the ability to reply/inject traffic captures with a varying degree of customisation. Desirable features regard the availability of an attack library, containing a list of pre-defined attacks, and the ability to import/create custom attacks.
- User Traffic & Activity Simulation – as required for specific scenarios depicting real environments with internal and client users. Examples are a virtual bank’s network with its information exchanges and transactions, a railway signalling network or an online retailer’s portal.
We have not discussed other relevant features of a cyber range towards the overall exercise experience, such as performance metrics, assessment criteria, instructor-led event management, etc. Every organization would ideally like to count on field-hardened security professionals, capable to train and deal with real cyber-attacks in an environment that is as close as possible to the one they are called to defend every day.
Ultimately, the ability to customize the cyber range simulation environment while practising on it over time is of paramount importance for the delivery of effective cyber security exercises.

CYBER RANGES PORTABLE Next-Gen Ruggedized Deployment - delivering Cross Cyber Exercises where it matters.
Conclusions
Next-generation cyber ranges are the sought-after solution to run large-scale exercises: they can deliver suitably engaging experiential content supplied by vendors off the shelf, custom-designed and built, directly in-house, by the same organization that needs to train its security professionals and confidentially test its own cyber resilience, or sourced from third-party subject matter experts and industry focused consultants.
Furthermore, cyber ranges are very much like game consoles. You may buy that console today because you like the games that come with it, but in a few months’ time you will want to play new and better games and you may want to support many more players. It is important to factor in the ability for new games development, licensing of new players and additional hardware requirements to scale over time. Indeed, next-generation cyber ranges are bound to become the game console of the future.
Dr. Al Graziano, CEO, Silensec | CYBER RANGES
 Dr. Graziano founded Silensec in Sheffield (UK) in 2006, after a successful career as the university course designer and then director of the first UK MSc. Information Security programme. An ISO 27001 certified cyber security company, Silensec has been delivering hands-on cyber drills to national CERT/CSIRT since 2014 in collaboration with the UN’s International Telecommunication Union. Silensec has developed the latest ITU Cyber Drill Framework. CYBER RANGES by Silensec is the only next-gen cyber range platform with its full feature set available on premise, on private and public cloud, and portable.
Dr. Graziano founded Silensec in Sheffield (UK) in 2006, after a successful career as the university course designer and then director of the first UK MSc. Information Security programme. An ISO 27001 certified cyber security company, Silensec has been delivering hands-on cyber drills to national CERT/CSIRT since 2014 in collaboration with the UN’s International Telecommunication Union. Silensec has developed the latest ITU Cyber Drill Framework. CYBER RANGES by Silensec is the only next-gen cyber range platform with its full feature set available on premise, on private and public cloud, and portable.
Silensec is a member of the European Cyber Security Organization (ECSO) and co-chairs the ECSO Working Group WG 5 on cyber ranges, cyber exercises and training, and also at sub-WG 5.1 (cyber ranges) and sub-WG 5.2 (education and training), furthering the best practice in the area of cyber ranges and cyber exercises.
Silensec is also a Premium Partner of the Global Cyber Alliance (GCA), based in NY, London and Brussels and focused on cooperation between industries and governments in tackling cybercrime.
Marcello Hinxman-Allegri CMktr SCIP, Head of Marketing & Business Development, Silensec | CYBER RANGES
 Marcello is a UK Chartered Marketer (CIM) and a professional member of the Society of Competitive Intelligence (SCIP). Marcello’s cyber security interests focus on computer risk assessment, insurance techniques … and Murphy’s law.
Marcello is a UK Chartered Marketer (CIM) and a professional member of the Society of Competitive Intelligence (SCIP). Marcello’s cyber security interests focus on computer risk assessment, insurance techniques … and Murphy’s law.
As a senior project manager, he worked on some of the UK’s largest cyber skills and e-learning developments, from community awareness to academic and vocational skills programmes, with a close focus on competencies and engaging multiple stakeholders: government agencies, corporate employers and industry associations, universities and colleges, schools, assessment & QA agencies, professional bodies, publishers and private training providers, edtech vendors.
Marcello co-chairs the European Cyber Security Organization’s SWG 5.2 on education and training.
Follow Us
Next-gen Cyber Ranges: delivering customer-specific repeatable large-scale realistic exercises