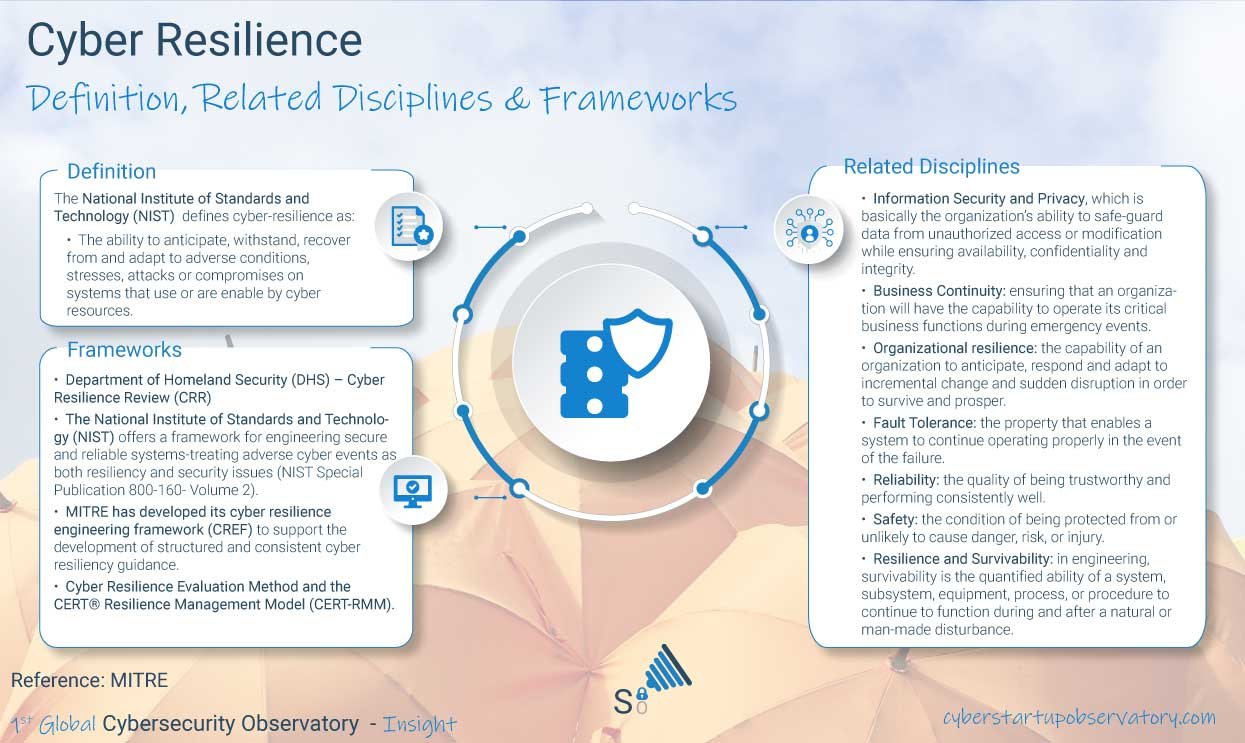
Power Grid Cybersecurity - where are we now?
Author: Jose Monteagudo, CEO, Smartrev Cybersec
There are many voices raising concerns about the fact that the quickly evolving threat landscape is outpacing protection measures and defences in the energy sector and  notably in the power grid.
notably in the power grid.
There are no shortcuts or easy ways to address the Power Grid Cybersecurity problem. Power grids are complex infrastructures that have been deployed during the last few decades. These grids are far more than generating stations, high voltage transmission lines, transformers and finally distribution lines that connect individual customers.
The overall architecture of the power grid includes seven different components which interact at different levels. These seven components will determine the ability of the power grid to change to address technical, operational, cyber security, market, regulatory or end-customer requirements.
These components are:
- Electric component: this is the most well-known piece of the jigsaw. It includes generators, transformers, switches, protection circuits, transmission and distribution lines to portray it in a simplistic way.
Industry component: including a huge number of utilities and other organizations interacting through operations, planning and markets. The structure of the markets will differ from region to region and will have important impact on the desire and ability to change. - Control component: including all the control systems, protection circuits and synchronization systems which are critical to safety, operational efficiency and performance.
- Digital component: composed of the information and communications systems (ICT) that allow monitoring and control of all the devices on the grid. The Digital layer is crucial for almost all business processes.
- Convergent networks: electricity generation will rely heavily on other networks that at a first glance seem to be un-related. This is the case of hydrocarbon fuels and natural gas pipelines, both critical for power generation.
- Regulatory component: as we might expect, the power industry is heavily regulated on multiple levels. The regulatory architecture will vary depending on the country and will also have an important effect on all operational aspects and in particular on cybersecurity which is the specific area of interest of this article.
- Coordination framework: for coordination and control of all the different elements and assets that make up the system, including some that are not owned by electric utilities.
From a topology perspective, the traditional power grid system is centralized and radial, where power is generated and delivered from one end to the other.
As we may see, there is huge complexity in the overall architecture of the power grid. There are many moving pieces that interact together and that have been built over the last few decades.
Moreover, this infrastructure wasn’t designed with cybersecurity in mind. Engineers at that time didn’t have to address the challenges that have been brought to the table by the new approach: connectivity everywhere.
So now we understand the architecture of the power grid a little bit more, the key question is how we can shape its evolution to cope with the very dynamic threat landscape.
The next generation power systems: the Smart Grid
The smart grid represents a major improvement over legacy power infrastructure. Leveraging state-of-the-art ICT technologies, it will enhance the efficiency and reliability of power systems, bringing distributed intelligence and demand response.
As we have discussed before, the topology of legacy power infrastructures was centralized and radial. Nevertheless, conventional methods for unidirectional power flow will no longer be effective to control renewable energy sources implemented at the consumption sector. Consequently, new strategies are needed to facilitate the bidirectional flow incurred by power production of the distributed energy resource units. The transformation will require intelligent distribution automation by means of decentralized power management as well as information and communications technologies.
With increased connectivity comes the major concern of cybersecurity. Arguably, we couldn’t have foreseen the cybersecurity challenge at the time of design of legacy electricity infrastructures. But in the case of the Smart Grid the situation is different. We have been well aware of the status quo with regards to the threat landscape. So, the question is, are next-gen electricity grids ready to face the current cybercrime reality?
Let’s take a look at the architecture of the Smart Grid to discuss the key security requirements and security challenges.
The Smart Grid can be structured in four different layers:
- Physical Layer: including Generation (cycling coal and natural gas-fired power plants with CCS, grid-based renewables, wind farms, nuclear power plants), Transmission, Distribution, Consumption and Grid-based Storage. The electrical flows are limited to this layer.
- Communication Layer: including home area, neighbourhood, access & black-hole, core, office and external networks.
- System Integration Platform: computing infrastructure, networks and security management, application and data integration.
- Software layer: meter data analysis (MDA), billing, outage management, load control, consumers and field engineers’ devices interface, GIS, wide area management systems, consumer information systems.
Additionally, we will also find the Industry and Regulatory elements as well as the 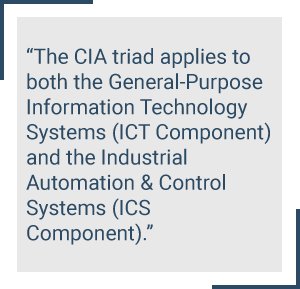 Coordination Framework as in the case of legacy electricity utilities.
Coordination Framework as in the case of legacy electricity utilities.
The security requirements for the Smart Grid are covered by the CIA Triad (Confidentiality, Integrity and Availability).
The CIA triad applies to both the General-Purpose Information Technology Systems (ICT Component) and the Industrial Automation & Control Systems (ICS Component). Nevertheless, when it comes to managing the risks, prioritization and strategy, it is important to differentiate between the ICT component and the Industrial Control Systems (ICS) component.
Let’s discuss the CIA Triad in detail:
- Availability: focuses on identifying and assuring data and services that need to be available. This is a critical aspect for Smart Grids systems supporting the Smart Grid automation, for example for SCADA servers of Distributed System Operators (DSO) or Transmission System Operators (TSO).
- Integrity, ensuring the fidelity of the information, which means identifying and preventing data to be modified without authorization. An example might be to guarantee that control commands and power control readings have not been
 modified during their transmission.
modified during their transmission. - Confidentiality, preventing unauthorized access to private information. This is less critical when considering grid automation systems (SCADA) but absolutely crucial for end consumers.
There are two other security dimensions that need to be considered: authentication and non-repudiation. Authentication has been considered implicitly in the CIA Triad and deals with making sure that someone or something really is who or what it claims to be. Non-repudiation refers to being able to prove that an action has been taken by the entity really responsible for that action. These two components are equally important for Industrial Automation & Control Systems (SCADA) and General-Purpose Information Technology Systems.
Power Grid Cybersecurity: challenges, threats and risks
Considering that ICT layers constitute roughly three quarters of the Smart Grid architecture, the major challenges below will be easily understood:
- Connectivity: as the topology of the Smart Grid is decentralized, all the elements require a high level of protection. The communication network, while allowing for significant advantages, also brings with it risks and challenges. It is key to striking a balance between internetworking and data security.
- Trust: consumers are no longer assumed to be trustworthy
- Privacy: the introduction of smart meters brings important challenges in terms of consumers’ information privacy.
- Software vulnerabilities: it is especially important to protect SCADA systems from malware, malicious updates as well as having a strict patching policy.
Cybersecurity in the Smart Grid must address not only deliberate attacks, but also inadvertent compromises of the information infrastructure due to user errors, equipment failures and natural disasters. Vulnerabilities might allow an attacker to penetrate a network, gain access to control software and alter load conditions to destabilize the grid in unpredictable ways.
Follow Us
Power Grid cybersecurity - where are we now?