Strong Approach to Cyber Secured Building and Energy Management Systems
Author: Daniel Ehrenreich, Consultant and Lecturer, SCCE
Introduction
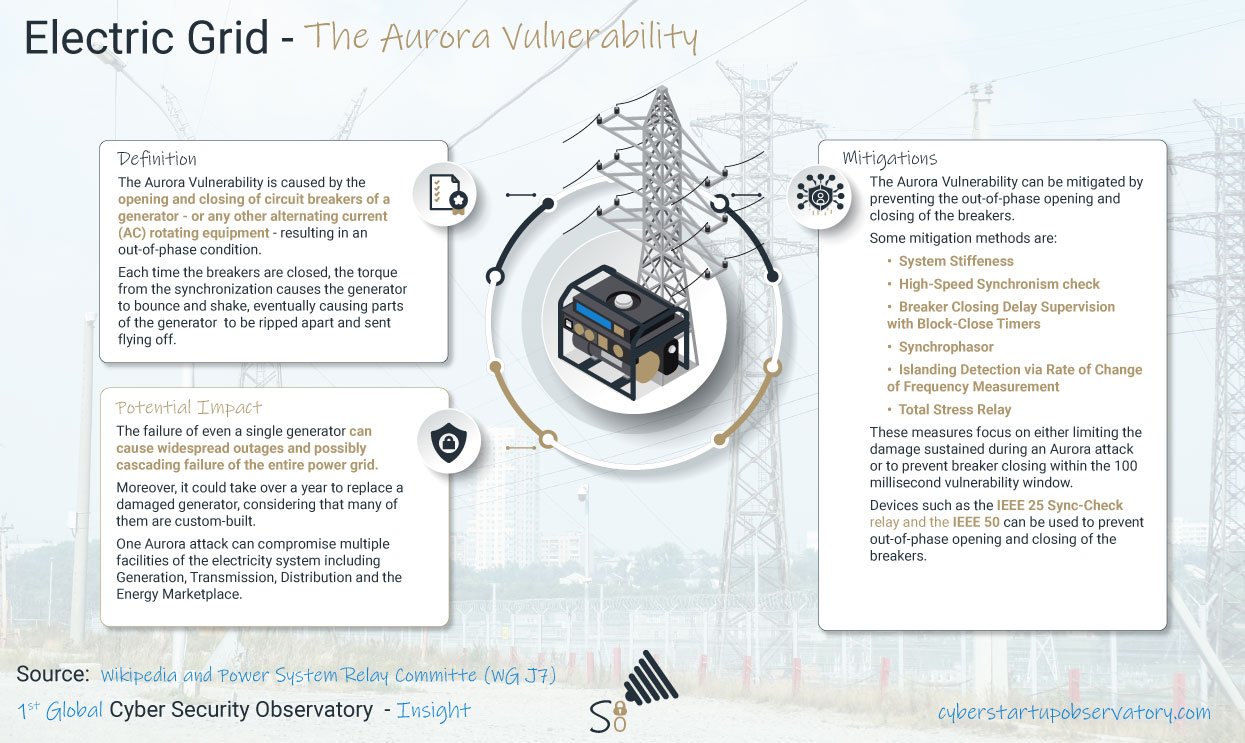
Cyber Secured Building Management Systems - The public attention directed to enhanced cyber security for office buildings and campuses is a growing. The reason driving these concerns is that an attacker might create a huge damage to any organization, for example by just causing the evacuation of the staff during working hours.
The control in these buildings is based on Building and Energy Management Systems (BEMS) which is managing a broad range of utility installations such as: feeders from the power grid, on-site generator, an uninterrupted power supply (UPS), heating, ventilation and air-conditioning (HVAC) system, water and sewage control, smoke and fire detection, CCTV surveillance, door locking, etc. Last but not least critical, in these floors you may also find the Data Center (DC), which holds critical information and must operate at high availability.
Deployment of reliable working utility equipment is important, but since there systems are monitored and supervised through BEMS computers, they must be equipped with adequate level of cyber defense solutions. Furthermore, their operation must be completely isolated from the internet in order preventing externally generated attack directed to interrupting the building activity.
Cyber risks in buildings
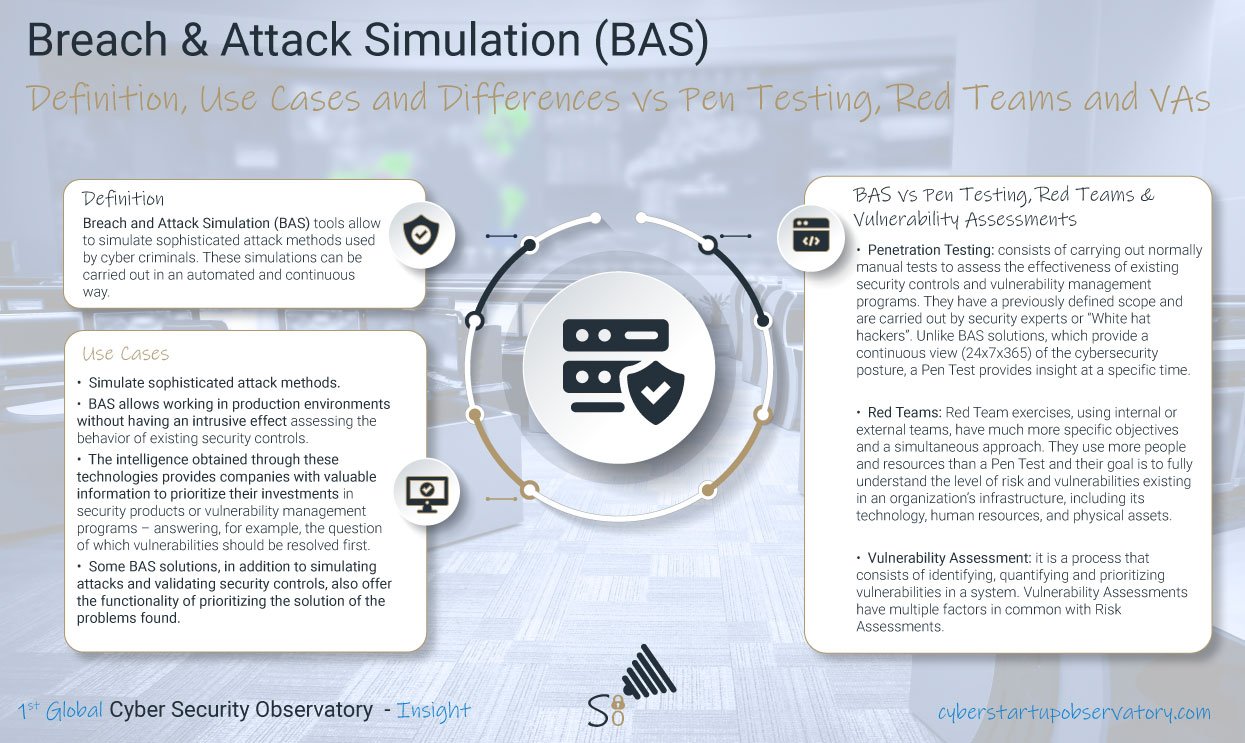
When dealing with the typical cyber threats directed to office buildings, you will learn about a broad range of vulnerabilities, created by low tier hardware and software and poorly secured architecture. Furthermore, you learn about subcontractors, driven by “project-profitability”, who push for using low-cost parts, weakly secured networks and their preference is always to use the same solutions which they did before.
Among the top cyber security risks in buildings you will find:
- Activation of smoke-fire alarms or a “false-positive” caused by a malfunction, might trigger evacuation from the building. Such an action might be intentionally caused by a disgruntled employee who has access to the system or by a maintenance person who might manipulate the fire alarm system.
- Interrupting the HVAC operation through the chiller controller or by remotely accessing the system through the BEMS computer. This action might be combined with intentional disabling of the the ventilation which is provided as an 2nd to best alternative to HVAC operation.
- Shutting down the lights in offices might create a panic response in spite the fact that the independent emergency lights in corridors turned on. Such attack might also be combined with intentional blocking the elevator operation and even with locking the fire doors in corridors.
- Shutting down the cooling of servers in the DC or activating the water sensing on the floor, might cause shut down of the DC and causing inconvenience and damage to people and organization who rely on that service. In worst case such manipulation might cause severe damage to the DC servers.
- Today CCTV cameras are installed in order to record what happens, detect critical events in buildings, pathways and secured facilities. If anyone gets access to the CCTV control, he might disable these cameras and even manipulate the pictures or video viewed in the control room.
Cyber defense for buildings
In buildings built for critical operations, you will find over a dozen of different and independent control operations. Some utilize simple embedded controllers in heavy machines such as the air-conditioning chiller, generator or a UPS. The BEMS is always deployed by an integrator and it supervises all the building operations and delivers critical-alerting information for operators in the security room.
The cyber security architect must worry about a range defense measures. Here are few examples:
- Quality of integrated controllers in HVAC machinery: Each such controller is linked to the SCADA system through DI/DO connections, and monitored via an RS-232 or LAN port using MODBUS or BACnet protocols. While this is not an obvious requirement, these standalone, often low-cost controllers must be internally protected against manipulation by an unauthorized person.
- Connection among control zones: In order to allow managing the building security through a centralized HMI, the isolated control zones must be integrated through strong cyber defense such as a SCADA-aware firewall or a Unidirectional Diode. The User Experience (UX) solution must conveniently fit to the operation processes and practices adopted by operators in the control room.
- Performing cyber-secured maintenance: This topic refers to connection of a maintenance laptops operated by an authorized serviceman. While most buildings rely on external experts, the laptop and the proprietary maintenance programs shall be owned by the building manager. Otherwise you are exposed to variety risks that your trusted maintenance person infects your system by his service computer.
- Deployment of Intrusion Detection System (IDS) and Visibility analyzer: In order protect the deployed BEMS you must maintain an accurate list of installed hardware and software versions and also see which PLCs exchange data each with other. The deployed IDS must analyze the communication and control processes, detect anomalies and effectively detect Zero-Day attacks.
- Physical security is an absolute precondition to cyber security. It is worth repeating that without strong attention to physical security, your cyber defense measures might not be effective. Physical security refers to your employees, visitors, vendors who deliver you updating programs in a USB stick or CD media. An adversary may access your network like it happened at Stuxnet in 2010.
- Hardening for all standard communications and control devices. Nowadays we use Commercially Off the Shelf (COTS) type hardware and software in most sections of the BEMS architecture. Therefore, all unused services and connection ports (hardware and software) must be disabled. Furthermore, all updates received from vendors must be scanned prior their deployment.
Summary
Building operators must be aware of potential harm created by attackers who aim to generate panic and evacuation. These threats might happen either through an internally generated attack by a disgruntled employee, service person or a visitor or through externally generated attacks through the internet after successful phishing attempts and compromising security barriers.
Last by not least, cyber security consultants must write realistic specifications, which on one hand are possible to implement and allow effective handling of incidents. The layered cyber defense for BEMS refers to best practices for system engineering, selecting quality PLCs, robust computers, cyber secured protocols, SCADA-ware firewalls, unidirectional diodes, visibility analysis programs, password management, conducting periodic security assessments and adequate processes for supply chain management.
Follow Us
Strong Approach to Cyber Secured Building and Energy Management Systems