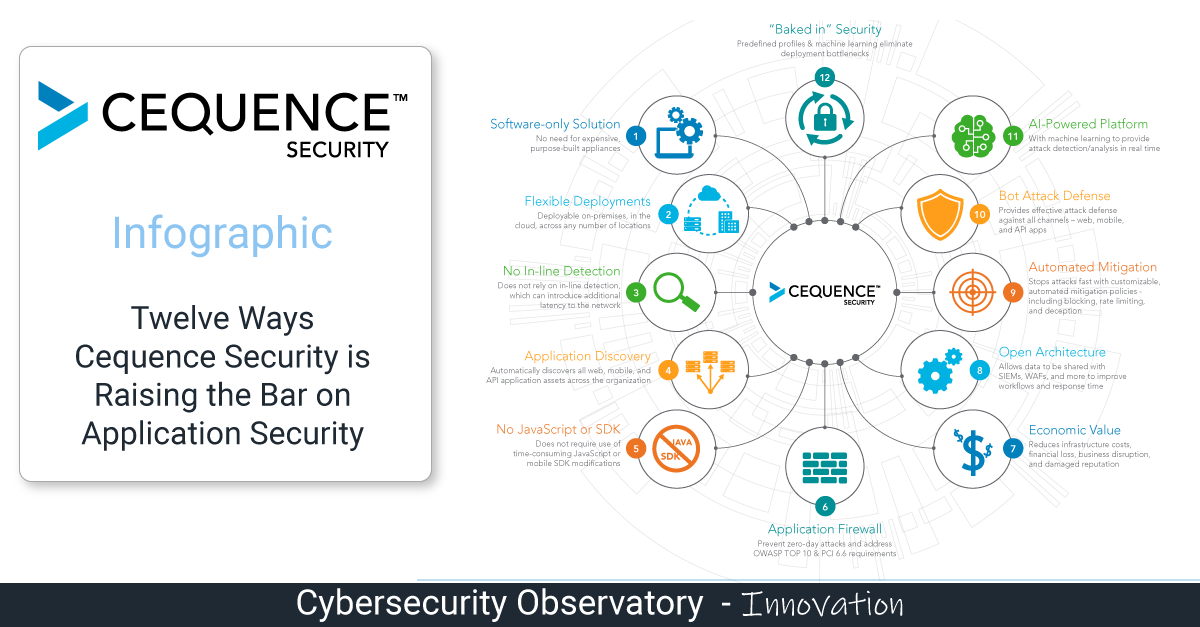
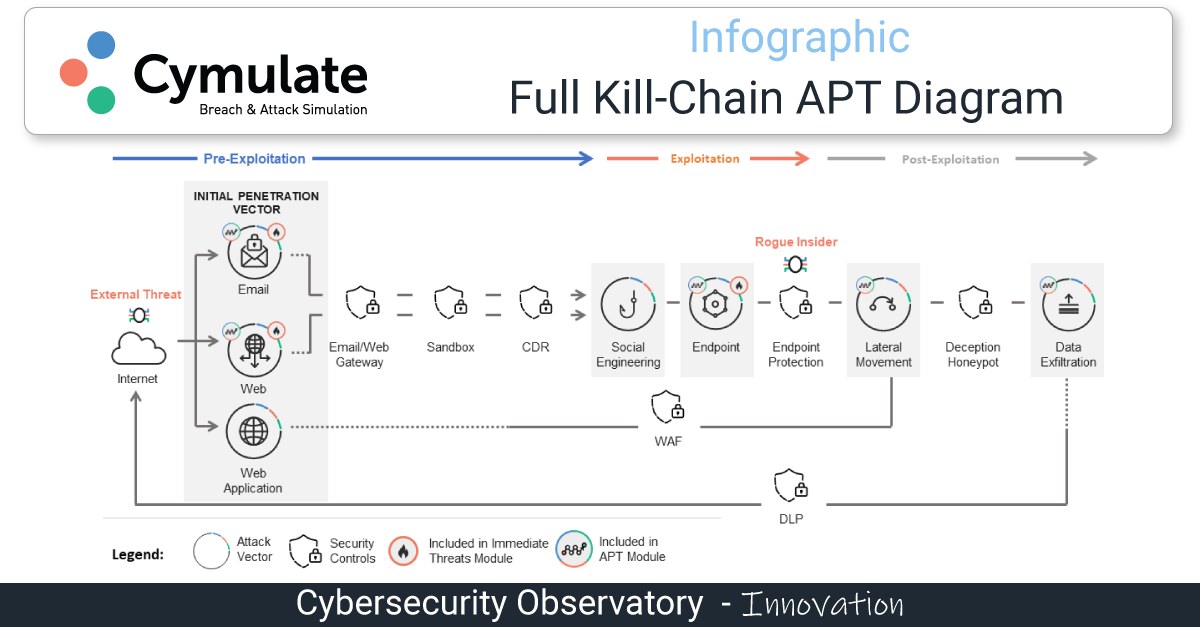
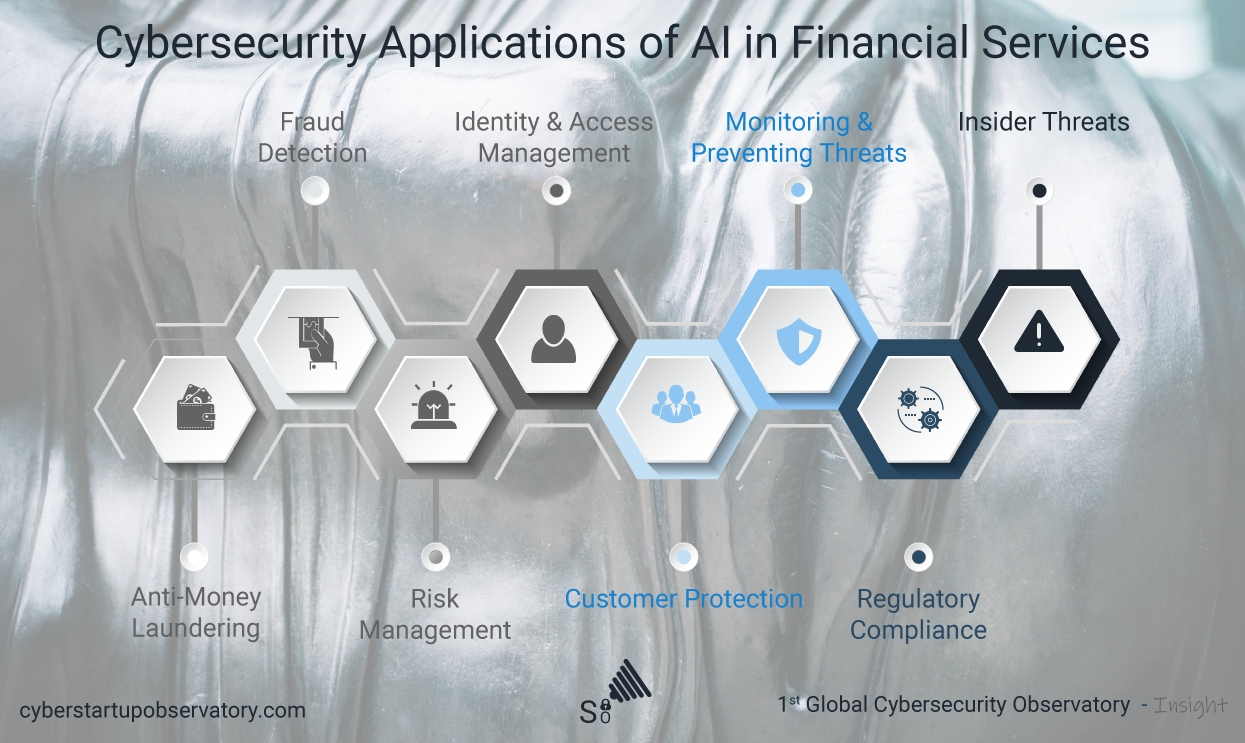
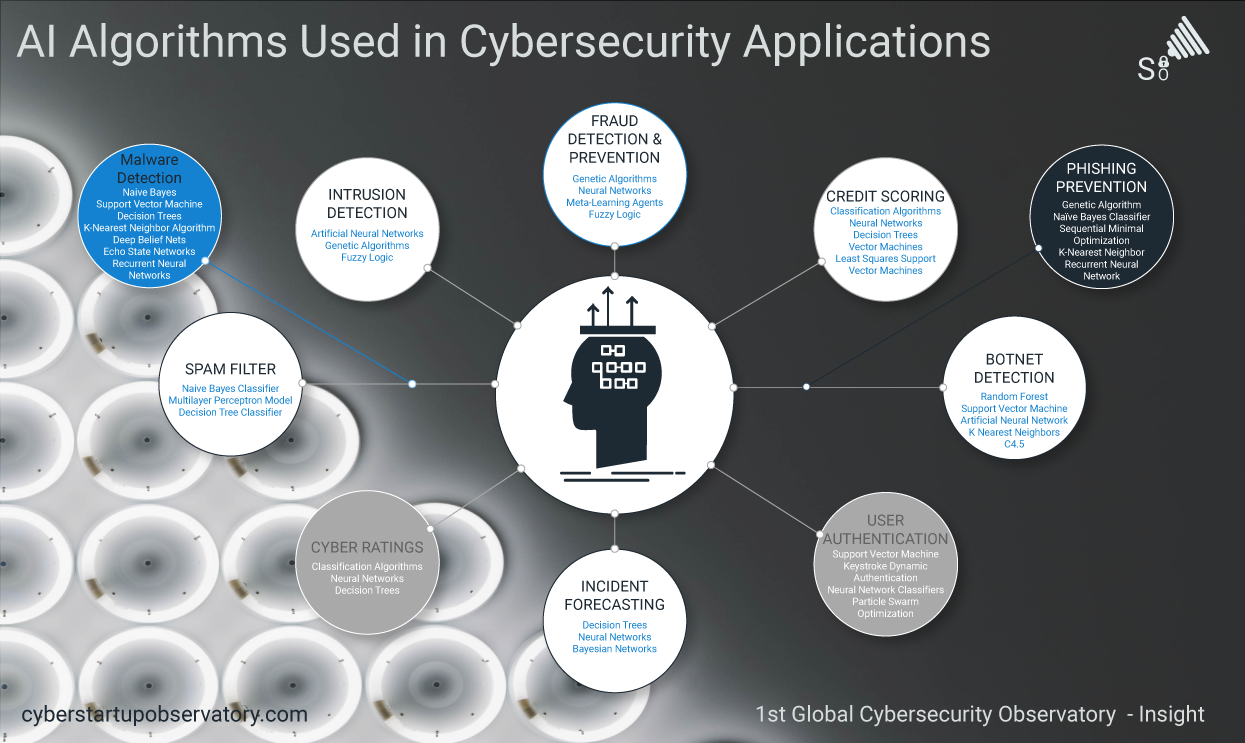
After a postgraduate diploma from Paris VII University (Scientific Information and Computer), and varied experience in the world of IT, I started to work in IT security, which was something new.
We are talking about a period when the internet was not used. However, I met very interesting and clever people that make me love this job. After this first experience, I joined Bull Machines as Telecommunication Project Leader. In this company, I also met some very interesting people and I made enough progress in my job to become company CISO.
After that, AccorHotels asked me to create an IT security department. I built the protection plan of the business, and have been managing it for more than 15 years. And it’s still very interesting, challenging and exciting.
What is your overall approach to information security?
My approach to IT security is first of all to practice risk analysis. What do we want to secure? Against who and what? What are the issues?
Once we have answered these questions, we can think about the solutions to put in place.
The company must have a minimum set of rules corresponding to the principles of the company’s security policy. On these mechanisms, you will be able to integrate your new system to secure. You must be able to add elements that can be technical but often organizational, yet you must also allow exceptions, to find the right balance between security and business.
Then your proposals may not be accepted for a number of reasons. It does not matter, there must be an arbitration organization to oversee this process.
This organization may also reject your proposal, which again, is acceptable. Most importantly, you have been able to present your risk analysis for this application and for the entire IS, even if your recommendations are not followed. If the company decides to take the risk it has the right to do so.
Of course, if you systematically lose then there is a problem. But I don’t hear about this kind of problem.
The CISO must light the road but he does not steer the bus, so he must say when there is risk and evaluate it and then if the company decides to go ahead against his opinion, he must start the second part of his job. This part is beginning to predict when the problem he sees coming will occur and how to allow the company to stay alive.
All this must be done via good communication with the governance structures of the company, so the CISO is no longer alone but it belongs to a team and security becomes a team game.
What should corporate boards know about conducting information security?
Communication about IT security incidents has evolved. Before we only found this type of information in specialized newspapers for geeks, but now you find this information in the economic press or in newspapers like Forbes or Fortune. Furthermore, we talk about it on television and in the different media. It becomes difficult for a board to ignore this type of problem.
The CISO must capitalize on it and explain why, when an incident comes out in the press, its business has not been hit or on the contrary why it has been and in this case what has been done to restart it.
Then there are the legal constraints. In most countries, IT security legislation has been strengthened and this is a legal requirement. It is therefore important to present the plans implemented and the possible gaps in relation to the legislation to the board
The third point is the budget. You have to be able to compare yourself to your competitors. This last point is a little bit challenging, as the amount of an IT security budget is quite difficult to determine. It might include participation from other departments in the form of workload or financial contribution. In addition, the size of the budget does not indicate that it is well used. However, this is a point that a Board can appreciate with its fair value with some good explanations.
How do you assess the responsibility of CISO for educating the workforce?
In terms of education, it is necessary to differentiate several aspects.
There is sensitization for the board, awareness for the rest of the workforce of the company and especially training for technicians. The first category is important because it allows for making the link with these presentations with members of the board around an IT security matter. People outside the company ideally close to government agencies must make this type of presentation. They have the competencies and the talent to speak to this audience.
Awareness must be made fun in order to avoid any anxiety and be done not all at once, but through regular interventions (video, email, incident communication and simple explanation) to create a safety culture without stress. Training is important and efficient, because the majority of technicians have a weak education in IT security. They know the basics, but are not necessarily aware of application security issues, for example. It seems important to me that the internal team in charge of application security provide this type of training. On the one hand, internal teams can take examples of the applications developed by the participants to explain their mistakes and improve their knowledge, while on the other hand as they are in the company and trained by them, technicians could ask them questions regularly without a question of paying, just around a coffee.
It should also be noted that these courses allow a company to be compliant with certain regulations.
Your business is only as strong as your weakest partner. Can you trust that your partners are keeping your data safe from attackers?
It is a good question. However, it is not new; this problem has been present for years.
When I created a team specialized in application security, with strong skills in pentest, I put them in the service of internal projects. This gave good results, as we came out of theoretical recommendations for practical demonstrations. It was no longer said. ‘there is a potential risk but now I have taken control of your application and that’s what I can do, so now you have to do this and that action’.
Our relations with the other teams, both IT and product, improved because they finally understood the risks they ran and the IT security team became an enabler and no longer a constraint. Given this result, I decided that systematically any new system that was to be installed on our IS should be tested by my teams. Moreover, the next step was naturally to test all the partners.
Today, it is part of our standard contracts to have to go through a pentest carried out by the Accor internal team before signing the contract. At first, it was a little complicated because all companies guaranteed a very high level of security. Nevertheless, in 90 percent of the cases there were breaches. I would say that today tests are accepted more easily, but there are still those who are recalcitrant and usually when we finally get the authorization, because otherwise they cannot work with us, it is often the least secure companies.
Of course, until everything is corrected we do not open into the partnership. And then, there are the control visits.
Why do some CISOs use technology for its cool factor instead of for securing or enabling the business?
I do not know if that is really the case. For my part, I do not think I’m exaggerating about technologies.
Indeed, each technology can cause new security problems on the one hand, and on the other hand is an additional source of failures. Generally, when we add a technology, we must always plan to double it to be the least blocking possible. We must also find experts in this technology, or train people. This makes the necessary budget quickly become important. If you tell me it’s the same problem for other IT departments; Competence, reliability, I would answer that in terms of security we are more demanding because we are the only department that is there to prevent problems. This is our goal. Therefore, if instead of limiting them we increase them, there is no reason to keep us. Moreover, I think that technology only meets 20% of a security problem, the remaining 80% are elsewhere; methods, processes or… old technologies.
I even think that technology is a trap. I have seen some companies stack the technological layers without any coherence. The result was painful for them. For me, the choice of a technology must be motivated by business and not by security
You’ve been in the industry for many years. What are some of the biggest changes you’ve seen in terms not only of threats, but also how cybersecurity is viewed in an organization?
The industry has of course changed. People, tools, methods of development have changed a lot. From my perspective, I find that we have become more and more specialized and at the same time, we understand the work of others less. There are more tools, but specialization often makes it difficult for people to adopt new and exciting tools.
The generalization of agile methods is also an important point. Agility is a process that helps teams provide quick answers about their project. Teams evaluate the project at regular meetings called sprinting, so how do you insert security into these new processes that change us from our traditional ways of doing security. For now, I’m testing different things. It is very interesting but I have not yet found the perfect integration of security.
The cloud also changes habits a lot; Solutions and specialties will disappear and be replaced. We need to be able to anticipate, to test ideas but I especially believe that companies must understand that we learn and walk while trying to find the right balance between security and efficiency and for this it must be that there is a right to error. However, with all the legal constraints that we have the legislator does not leave much room for this right.
Besides that, attacks and hackers have many more ways to cause damage. We used to say that hackers are professionalized, which is probably true, but it is also true that it is easier today to become a professional hacker. It is quite easy to find powerful tools, courses, sharing experience… it is perhaps in this sense that they are more professionalized.
We are at cross-roads, the opponent is stronger, and we must move quickly and find the right systems of protections. However, I remain optimistic.
Since IT security became a necessity, CISO had to reinvent itself several times. Technologies are changing, new risks are appearing with more and more important impacts. As said before, we are in a complicated period, where we want to develop faster and faster with important rights and often without being sure of being able to control everything. We must find new ways of doing things. It reminds me of the beginnings of the use of the Internet, where we had practically no tools to protect IS, very few skills to use them and where the users did not understand what we were protecting ourselves against. However, we succeeded, with methods and tricks to overcome the challenges. Therefore, I think we can do it again. Specially because the IT security community is passionate and knowledgeable people who love and embrace challenges.