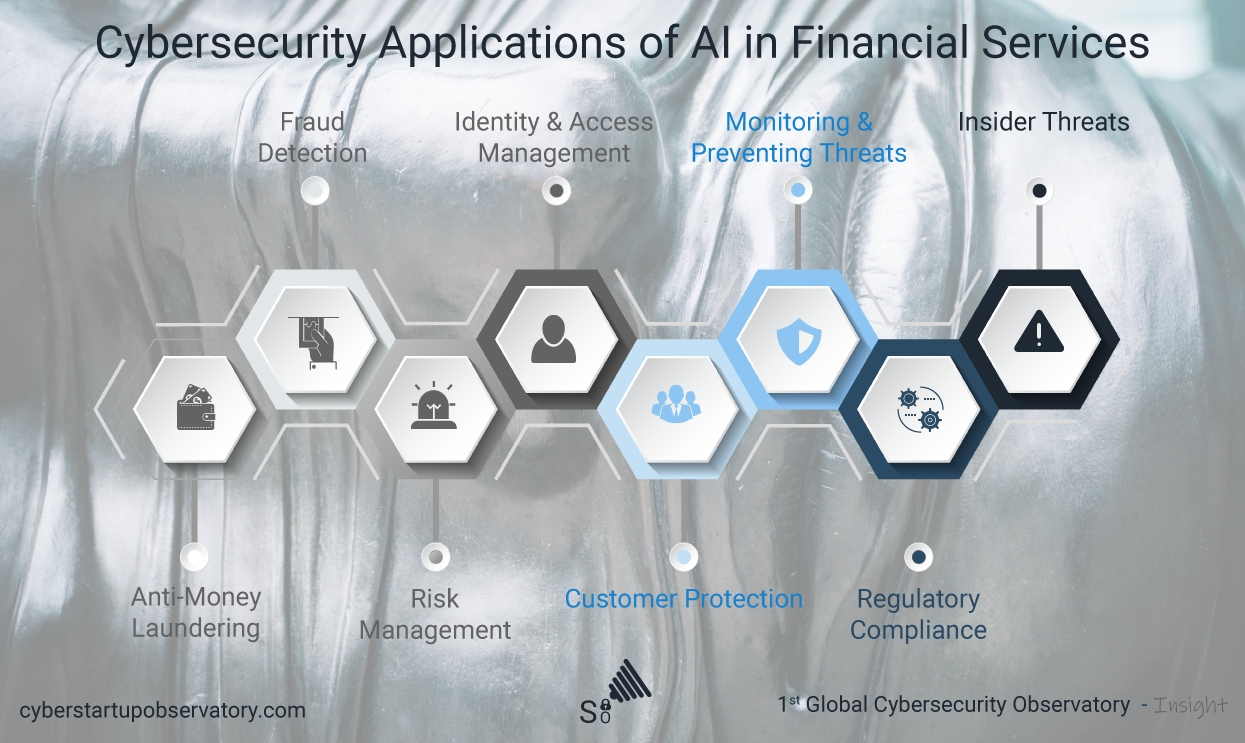
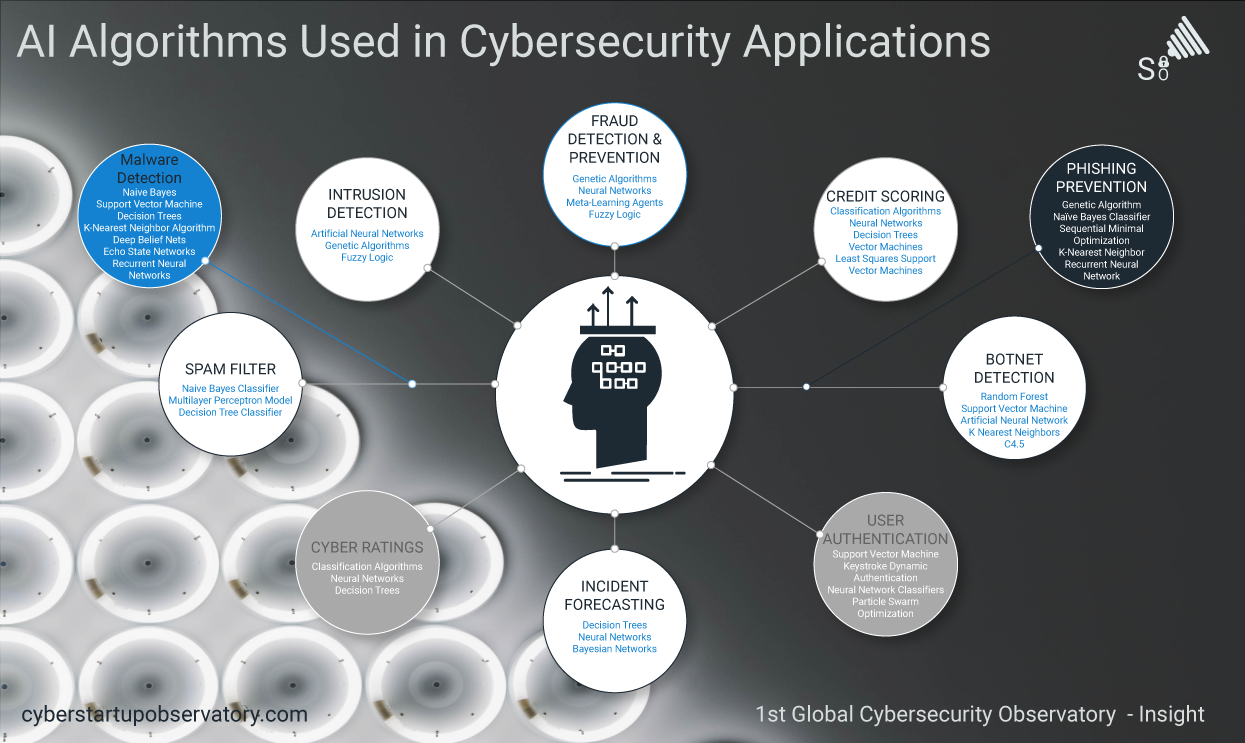
The increasing use of multiple digital devices, the access to professional and private social … [Read more...]
Foundations for a successful Identity and Access Management Program
Identity and Access Management (IAM) relies primarily on getting answers to three basic yet complex … [Read more...]
Stop blaming your users for compromised credentials
Stop blaming your users for compromised credentials Users remain the biggest threat to a company’s … [Read more...]
Security and Privacy? With Active Behavioural Biometrics it is Possible
Security and Privacy? With Active Behavioural Biometrics it is Possible. Having the privilege to … [Read more...]