The Breach & Attack Simulation (BAS) technology Revolution
Cyberattacks have evolved dramatically in the past couple of decades regarding their capabilities, scope, fallout, number of targets, etc. The worldwide damages from cybercrime are reaching all-time highs and it looks that this will only get worse. Since the risk of being attacked is so high, C-level managers and executives are looking to boost their organization’s security posture. CIOs and CISOs are now pressured to prioritize cybersecurity and shift budget to acquiring additional security solutions making sure that they are resilient to cyberattacks.
Since testing the cybersecurity posture of organizations is becoming a top priority, it triggered an increased demand for the latest and most comprehensive testing solutions. Traditional ways of testing include scanning for vulnerabilities (which entails checking for vulnerabilities that are already known or that have already been exploited by cybercriminals), manual penetration testing (consisting of pen tests that are conducted by human testers who try to evaluate the security of an organization’s infrastructure by safely exploiting vulnerabilities), and Red Team testing (where a Red Team consisting of cybersecurity pros attacks the organization’s network, and a Blue Team consisting of IT managers and/or cybersecurity staff will try to stop these attacks).
In its Hype Cycle for Threat-Facing Technologies 2017, Gartner introduced a new domain: The Breach & Attack Simulation (BAS). Gartner defines Breach & attack Simulation (BAS) technologies as tools “that allow enterprises to continually and consistently simulate the full attack cycle (including insider threats, lateral movement and data exfiltration) against enterprise infrastructure, using software agents, virtual machines, and other means”. What makes BAS special, is its ability to provide continuous and consistent testing at limited risk and that it can be used to alert IT and business stakeholders about existing gaps in the security posture or validate that security infrastructure, configuration settings and detection/prevention technologies are operating as intended. BAS can also assist in validating if security operations and the SOC staff can detect specific attacks when used as a complement to red team or penetration testing exercises.
 In its Hype Cycle for Threat-Facing Technologies 2018, Gartner rated the benefit of BAS as “high”. As an emerging technology, it is expected to go mainstream within the next 10 years. Last year, Gartner predicted that it would take more than 10 years, which underpins the acceleration of BAS as becoming a mainstream technology and that the BAS market is proving the value and accuracy of security assessments resulting from simulated attacks. The installed base has approached hundreds of customers for leading BAS vendors in 2018. In its previous report, Gartner found that “only a few vendors having real customer deployments”. It illustrates that CISOs are allocating budget for automated testing and assessment of existing security controls as well as the appropriate configuration settings for email and web security gateways, firewalls and web application firewalls, and ACLs.
In its Hype Cycle for Threat-Facing Technologies 2018, Gartner rated the benefit of BAS as “high”. As an emerging technology, it is expected to go mainstream within the next 10 years. Last year, Gartner predicted that it would take more than 10 years, which underpins the acceleration of BAS as becoming a mainstream technology and that the BAS market is proving the value and accuracy of security assessments resulting from simulated attacks. The installed base has approached hundreds of customers for leading BAS vendors in 2018. In its previous report, Gartner found that “only a few vendors having real customer deployments”. It illustrates that CISOs are allocating budget for automated testing and assessment of existing security controls as well as the appropriate configuration settings for email and web security gateways, firewalls and web application firewalls, and ACLs.
To recap: The BAS domain is expected to continue its meteoric rise since BAS tools show organizations if their cybersecurity really works. To quote Gartner: “The ability to provide continuous testing at limited risk is the key advantage of BAS technologies, which are used to alert IT and business stakeholders about existing gaps in the security posture, or validate that security infrastructure, configuration settings and prevention technologies are operating as intended“.
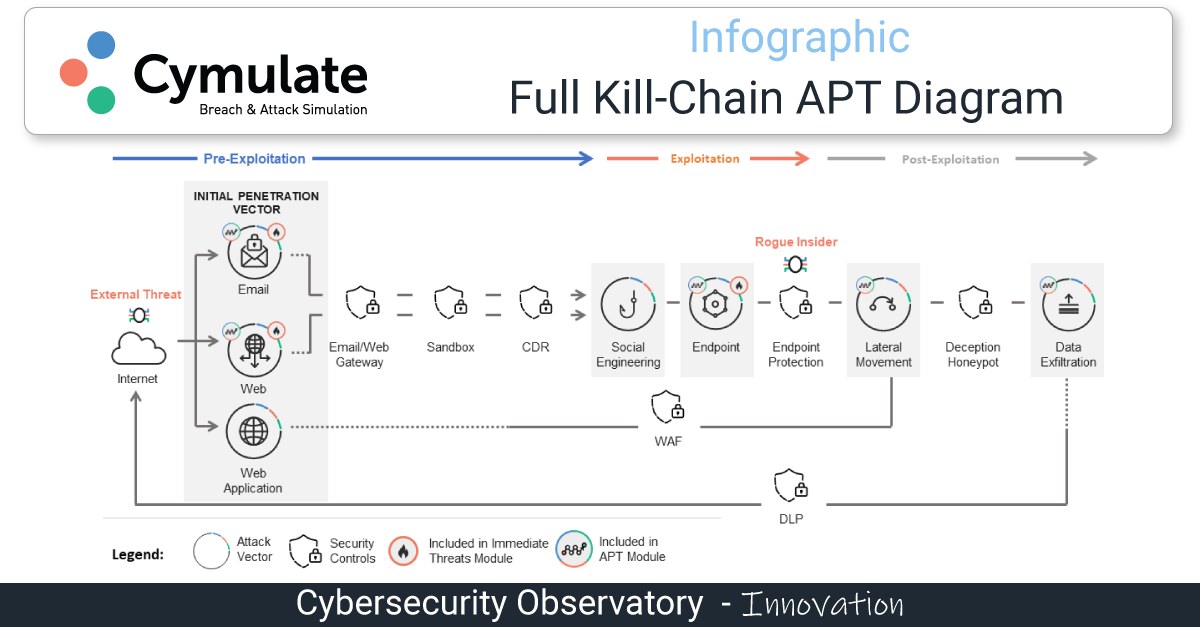
Cymulate
One of the leaders in the BAS tech arena, is Cymulate. With its easy-to-use BAS platform, it helps companies to stay one step ahead of cyber attackers. It mimics the myriad of attack strategies and tools that malicious hackers and cyber criminals deploy, allowing businesses to assess their true preparedness to handle cybersecurity threats effectively. Since it’s an on-demand SaaS-based platform, it lets users run simulations 24/7 from anywhere, which shortens the usual testing cycle and speeds up the time to remediation.
The capabilities and functions of Cymulate’s BAS platform include:
- The ability to test all phases of an attack, from pre-exploitation to post-exploitation, persistence and maintaining access;
- The ability to test continuously, periodically and on-demand;
- The ability to deliver safe tests without interfering with business operations;
- The ability to test both perimeter and internal security controls;
- The ability to update continuously to deliver simulations that also include in-the-wild detected threats;
- The ability to provide comprehensive conclusive reports including recommendations for mitigation.
***Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.